Teleport Cloud Audit Logs
These logs are emitted by Teleport Cloud to an S3 bucket and it's worth noting that the setup process on the teleport cloud side is slightly unique compared to other providers. They will ask you to run several commands in AWS Cloud Shell to instantiate a collection of teleport buckets.
At the end of the process you should be have a new bucket called something like:
xxxxxxxx-longterm-zzzzzzzzz-zzzz-zzzz-zzzz-zzzzzzzzzzzzThis is the bucket you'll provide RunReveal with access to.
1. Create an integration with teleport to your bucket
Their docs are available online, but under Enroll New Integration, you'll need to set up a next AWS External Audit Storage integration.
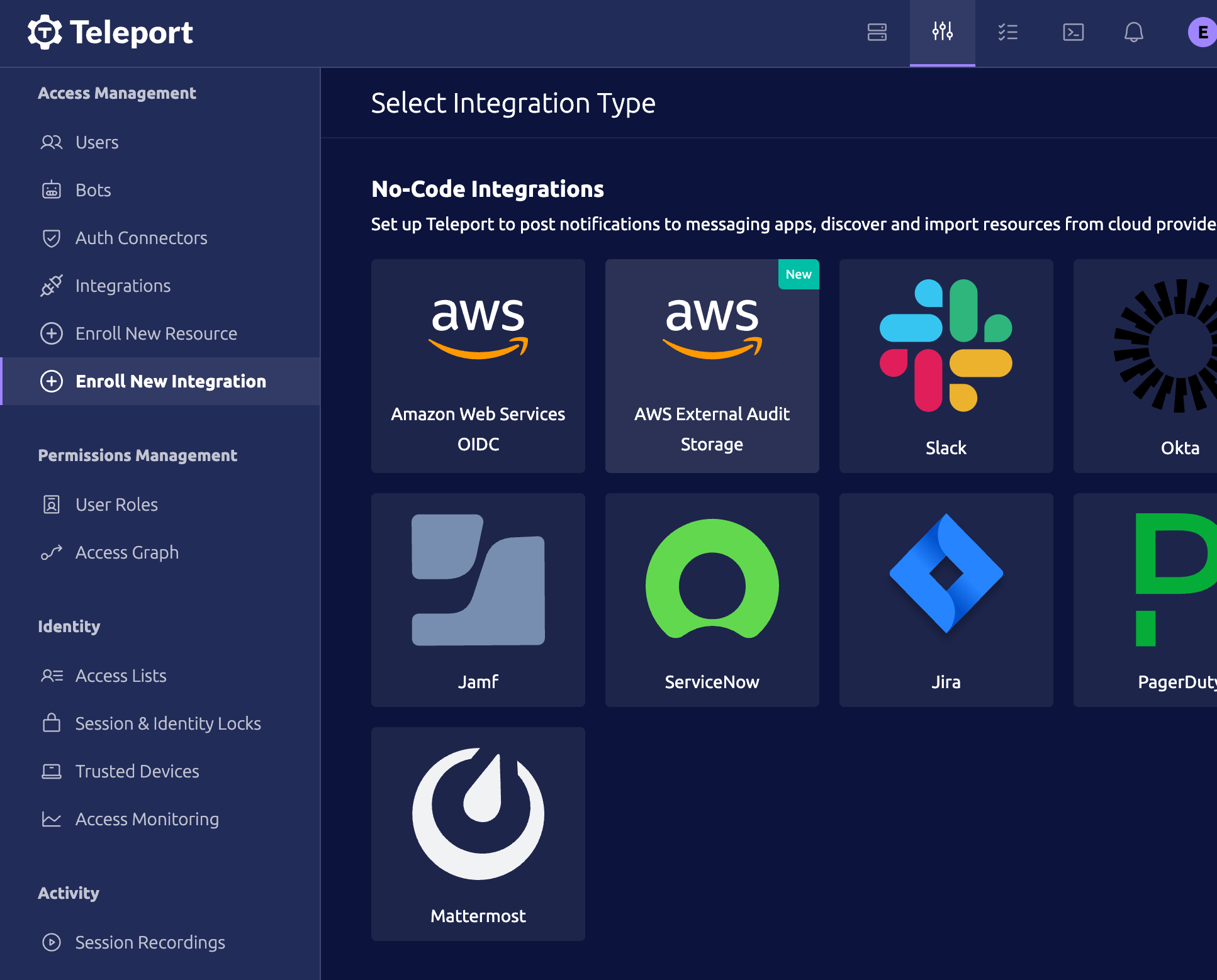
As part of the setup process, you'll provide teleport with a name for your integration, the iam role name you'd like for teleport to create, the bucket name you'd like teleport to create, and the bucket prefix.
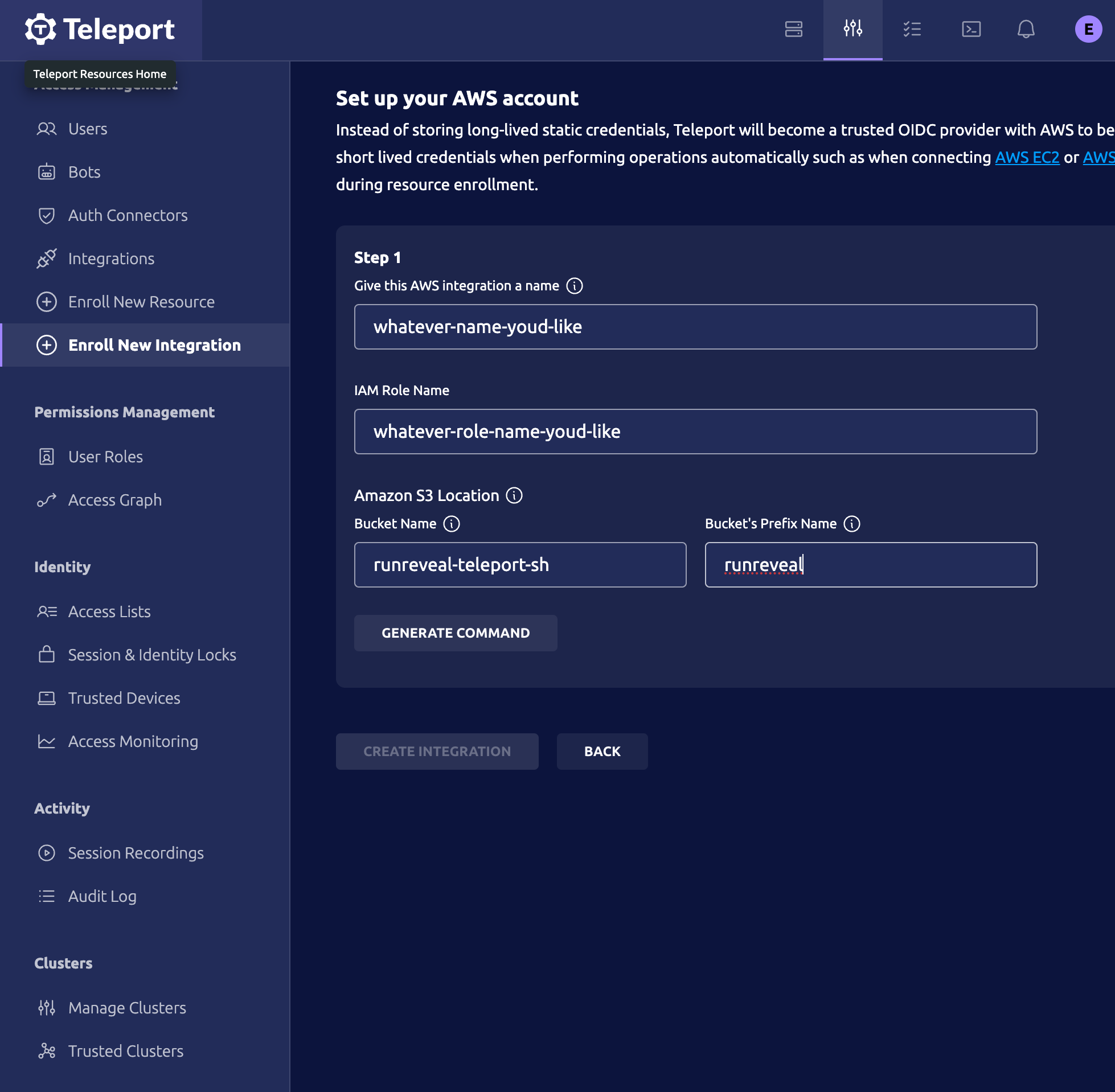
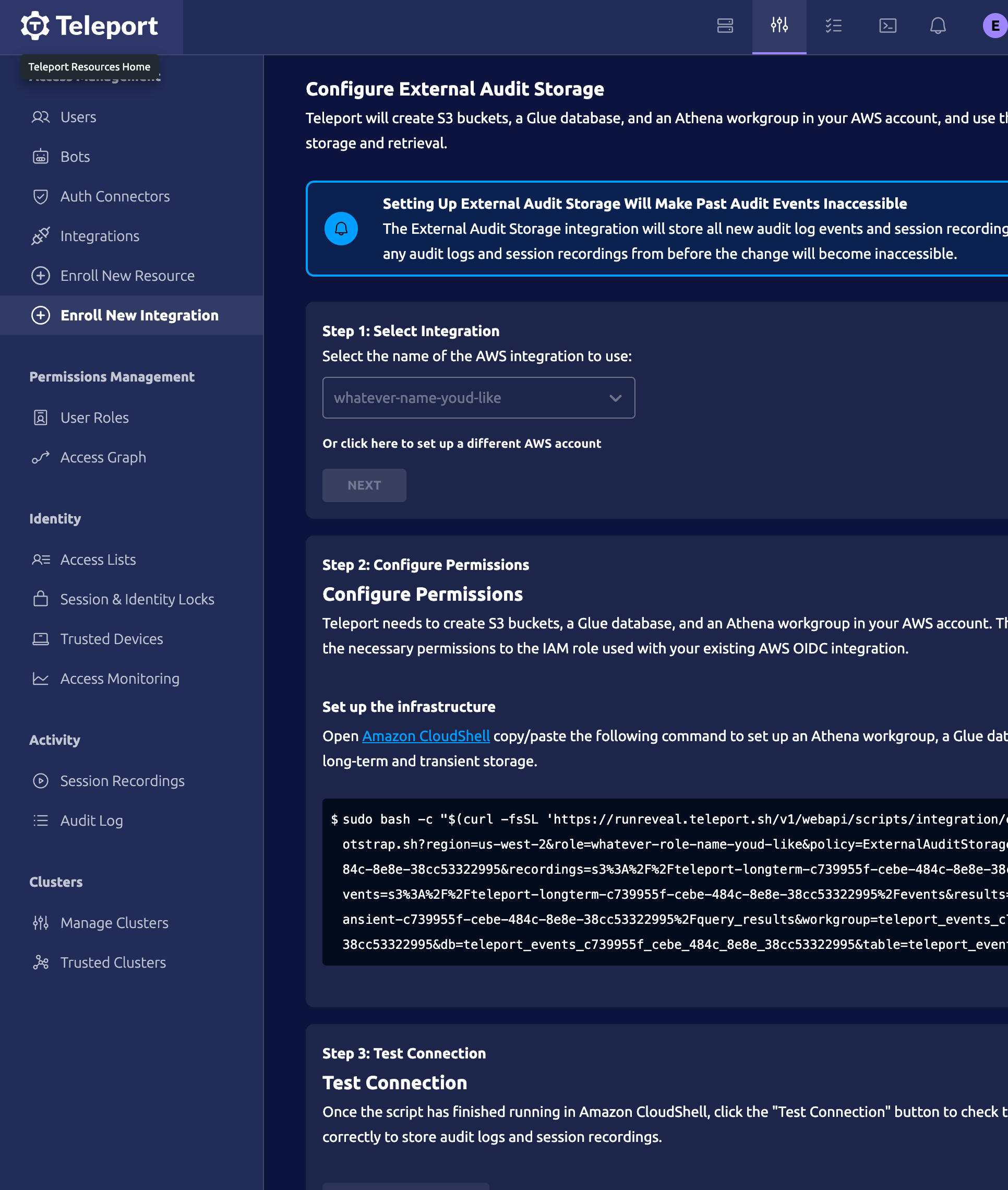
Once you provide these bits of information, you'll be given a Amazon CloudShell command to run. This will create the role and the bucket within your AWS account. Once you provide teleport with your role's name, including the AWS account ID.
Once you provide teleport with this information they will ask you to continue with the integration by running an Amazon CloudShell command one final time to provision your buckets, and finally test the connection.
2. Normal RunReveal S3 Setup
Provide RunReveal with the role name, external ID, and bucket name that teleport is writing to.
Keep in mind, teleport will create multiple buckets in your account and the bucket we will read
from is the one that contains the word longterm, like this example:
xxxxxxxx-longterm-zzzzzzzzz-zzzz-zzzz-zzzz-zzzzzzzzzzzzOnce you find that bucket, create the normal event notification for that bucket to write to our SNS queue.
arn:aws:sns:<REGION>:253602268883:runreveal_teleport