Configuring Role Based Access Control
RunReveal supports Role Based Access Control for subjects accessing resources in your workspace.
We have configured a set of default roles to simplify the management of permissions assignment to users through those roles.
Each resource has permissions defined for Read and Edit actions. Read allows read-only access to the class of resources including listing the instances of that resource. Edit allows for creation, updating, and deletion of resources (delete is included in edit permissions).
The following roles have been defined for workspaces: admin, analyst, operator and cibot. Below you will see their permissions enumerated.
| Permission | Description | Admin | Analyst | Operator | CIBot |
|---|---|---|---|---|---|
| Read Workspaces | View workspace information and members | ✅ | ✅ | ✅ | |
| Edit Workspaces | Modify workspace settings and members | ✅ | |||
| Read Sources | View data sources and configurations | ✅ | ✅ | ✅ | |
| Edit Sources | Create, modify, and delete data sources | ✅ | |||
| Read Destinations | View destination configurations | ✅ | ✅ | ✅ | |
| Edit Destinations | Create, modify, and delete destinations | ✅ | |||
| Read Queries | Run queries and view detections | ✅ | ✅ | ✅ | ✅ |
| Edit Queries | Create, modify, and delete queries and detections | ✅ | ✅ | ✅ | ✅ |
| Read Parameters | View parameter configurations | ✅ | ✅ | ✅ | |
| Edit Parameters | Create, modify, and delete parameters | ✅ | ✅ | ✅ | |
| Read Investigations | View investigation data | ✅ | ✅ | ✅ | |
| Edit Investigations | Create and modify investigations | ✅ | ✅ | ✅ | |
| Read Filters | View filter configurations | ✅ | ✅ | ✅ | |
| Edit Filters | Create, modify, and delete filters | ✅ | |||
| Read Enrichments | View enrichment configurations | ✅ | ✅ | ✅ | ✅ |
| Edit Enrichments | Create, modify, and delete enrichments | ✅ | ✅ | ✅ | |
| Read Notifications | View notification configurations | ✅ | ✅ | ✅ | |
| Edit Notifications | Create, modify, and delete notifications | ✅ | |||
| Read Dashboard Layouts | View dashboard configurations | ✅ | ✅ | ✅ | |
| Edit Dashboard Layouts | Create, modify, and delete dashboards | ✅ | |||
| Read Topics | View topic configurations | ✅ | ✅ | ✅ | |
| Edit Topics | Create, modify, and delete topics | ✅ | ✅ | ||
| Create Tokens | Create workspace tokens and API keys | ✅ | ✅ | ✅ | |
| Manage Sessions | Manage user sessions | ✅ | |||
| Read Chat | View chat conversations and history | ✅ | ✅ | ✅ | |
| Edit Chat | Create new chats and send messages | ✅ | ✅ | ✅ | |
| Read Custom Views | View custom views and use them in queries | ✅ | ✅ | ✅ | |
| Edit Custom Views | Create, modify, and delete custom views | ✅ | ✅ | ||
| Read Custom Roles | View custom role configurations and assignments | ✅ | |||
| Edit Custom Roles | Create, modify, and delete custom roles | ✅ |
Custom Roles
Custom roles provide fine-grained access control by combining UI/API permissions with data-level restrictions. Use them to implement least-privilege access, segment teams by data source, or create read-only analyst roles.
Navigate to Settings → Custom Roles to view, create, and manage custom roles.
Feature Flag Required: Custom Roles is currently gated behind a feature flag. Please reach out to RunReveal support to request access to this feature.
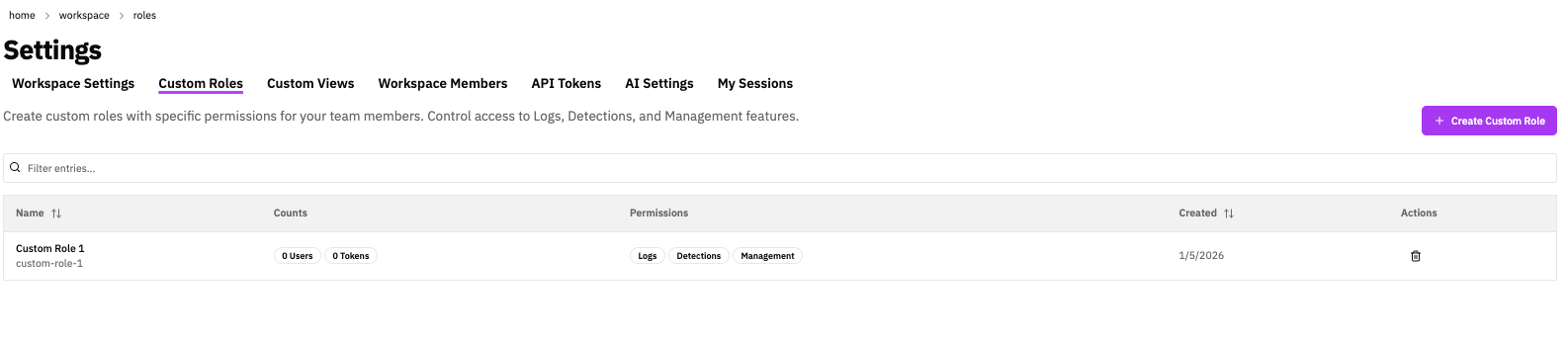
Creating a Custom Role
Click + Create Custom Role to open the role configuration form.
Basic Information:
| Field | Required | Description |
|---|---|---|
| Display Name | Yes | Human-readable identifier (auto-generates URL slug) |
| Description | No | Document the role’s intended purpose |
UI/API Permissions
Control which RunReveal features and API endpoints the role can access.
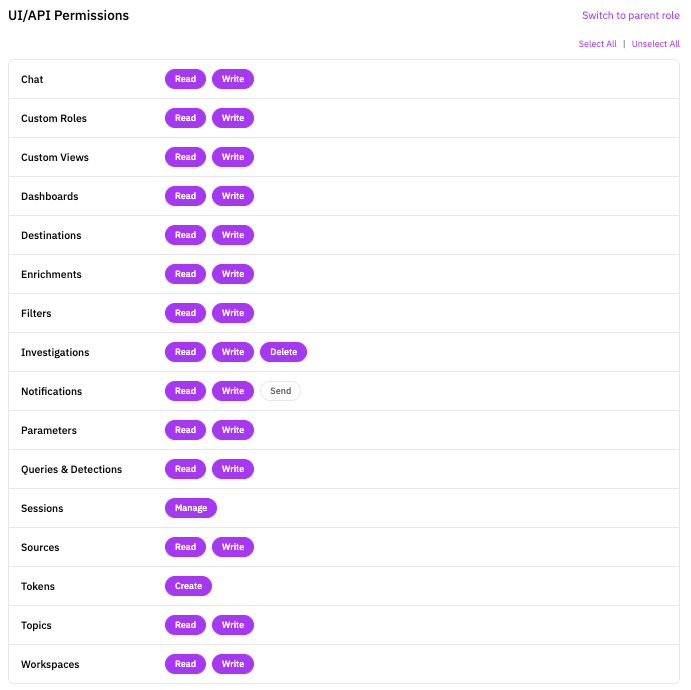
Configuration Options:
| Option | Description |
|---|---|
| Inherit from parent role | Copy all permissions from a default role (Admin, Analyst, Operator, or CIBot) |
| Custom permissions | Select specific permissions per resource |
When using custom permissions, toggle individual actions for each resource:
| Resource | Actions | Notes |
|---|---|---|
| Chat | Read, Write | AI chat interface access |
| Custom Roles | Read, Write | View and manage custom roles |
| Custom Views | Read, Write | Saved query views |
| Dashboards | Read, Write | Dashboard creation and viewing |
| Destinations | Read, Write | Log destination configuration |
| Enrichments | Read, Write | Enrichment rule management |
| Filters | Read, Write | Log filter configuration |
| Investigations | Read, Write, Delete | Investigation management with delete capability |
| Notifications | Read, Write, Send | Notification config and manual sending |
| Parameters | Read, Write | Workspace parameters |
| Queries & Detections | Read, Write | Detection rules and saved queries |
| Sessions | Manage | User session management |
| Sources | Read, Write | Log source configuration |
| Tokens | Create | API token generation |
| Topics | Read, Write | Topic management |
| Workspaces | Read, Write | Workspace settings |
Use Select All or Unselect All to quickly configure permissions, then adjust individual resources as needed.
Data Access
Control access to workspace data through three independent toggles.
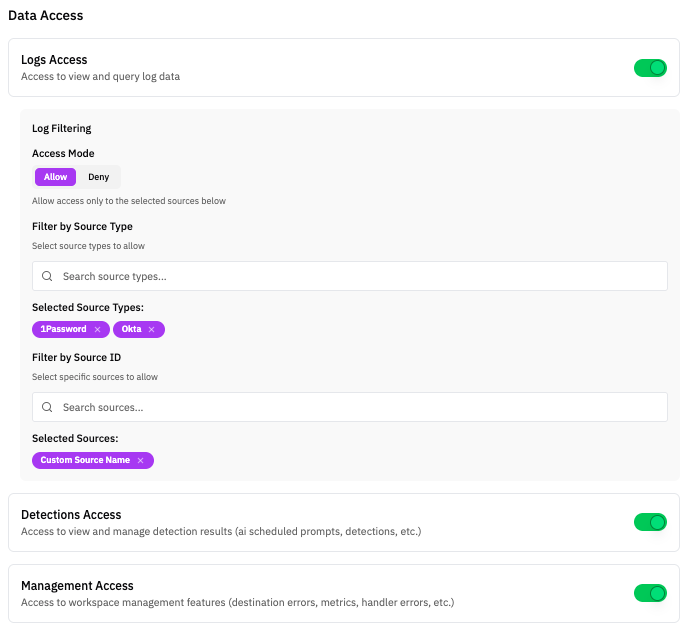
| Access Type | Description |
|---|---|
| Logs Access | View and query log data. When enabled, expands Log Filtering options. |
| Detections Access | View and manage detection results, AI agents, and detection configurations. |
| Management Access | Access workspace management features including destination errors, metrics, and handler errors. |
Log Filtering
When Logs Access is enabled, configure which log sources the role can access.
Access Mode:
| Mode | Behavior |
|---|---|
| Allow | Whitelist — role can only access selected sources |
| Deny | Blacklist — role can access all except selected sources |
Filter Criteria:
| Filter | Use Case |
|---|---|
| Source Type | Restrict by log type (e.g., only 1Password and Okta logs) |
| Source ID | Restrict to specific source instances (e.g., a single AWS account) |
Filters are additive: if you select both source types and source IDs, the role can access logs matching either criterion.
Role List Columns
The Custom Roles list displays:
| Column | Description |
|---|---|
| Name | Display name and slug identifier |
| Counts | Number of users and API tokens assigned to this role |
| Permissions | Badges indicating enabled data access (Logs, Detections, Management) |
| Created | Role creation date |
| Actions | Delete role (requires customRoles#write permission) |
Common Use Cases
| Scenario | Recommended Configuration |
|---|---|
| Security analyst (read-only) | Logs + Detections Access enabled; all UI permissions set to Read only |
| SOC tier-1 | Allow mode with specific source types; Detections Access enabled; no Management Access |
| External consultant | Deny mode excluding sensitive sources; limited UI permissions |
| DevOps team | Allow mode for infrastructure sources only (CloudTrail, Kubernetes); Sources Read/Write enabled |
| Compliance auditor | Logs + Detections Access (read-only); no write permissions |
Permissions Required
| Action | Required Permission |
|---|---|
| Create, edit, delete custom roles | Custom Roles: Write |
| View custom role configurations | Custom Roles: Read |
Role Inheritance: Custom roles can inherit permissions from default roles, but default roles cannot inherit from custom roles. This ensures default role behavior remains stable and predictable.
Assigning Custom Roles
Assign custom roles to new users at Settings → Workspace Members by clicking “Invite Member”. Custom roles appear in the role dropdown alongside default roles (Admin, Analyst, Operator, CIBot).
Custom roles can also be assigned to API tokens at Settings → API Tokens to scope programmatic access.