Authentication
Standing up a BYOC environment requires a few steps. Since our product will be running within your VPC, dependencies on our systems for authentication and authorization don’t really make sense. Instead our product can be configured to use the same authentication and authorization methods you use in a cloud deployment but within your VPC.
The login process is governed by environment variables. The following need to be set in your environment depending on the authentication method you’d like to use.
GOOGLE_CLIENT_ID=google
GOOGLE_CLIENT_SECRET=google
MICROSOFT_CLIENT_ID=microsoft
MICROSOFT_CLIENT_SECRET=microsoft
GITHUB_CLIENT_ID=github
GITHUB_CLIENT_SECRET=githubLog in with Google
To configure Google authentication, you’ll need to create a project in the Google Cloud Console and enable the Google OAuth API. You’ll also need to create a client ID and secret for your project.
- Create a project in the Google Cloud Console.
- Enable the Google OAuth API if necessary.
- Create a client ID and secret for your project. The authorized redirect URI should be the URL of your RunReveal API, the authorized origin should be the URL of your RunReveal API.
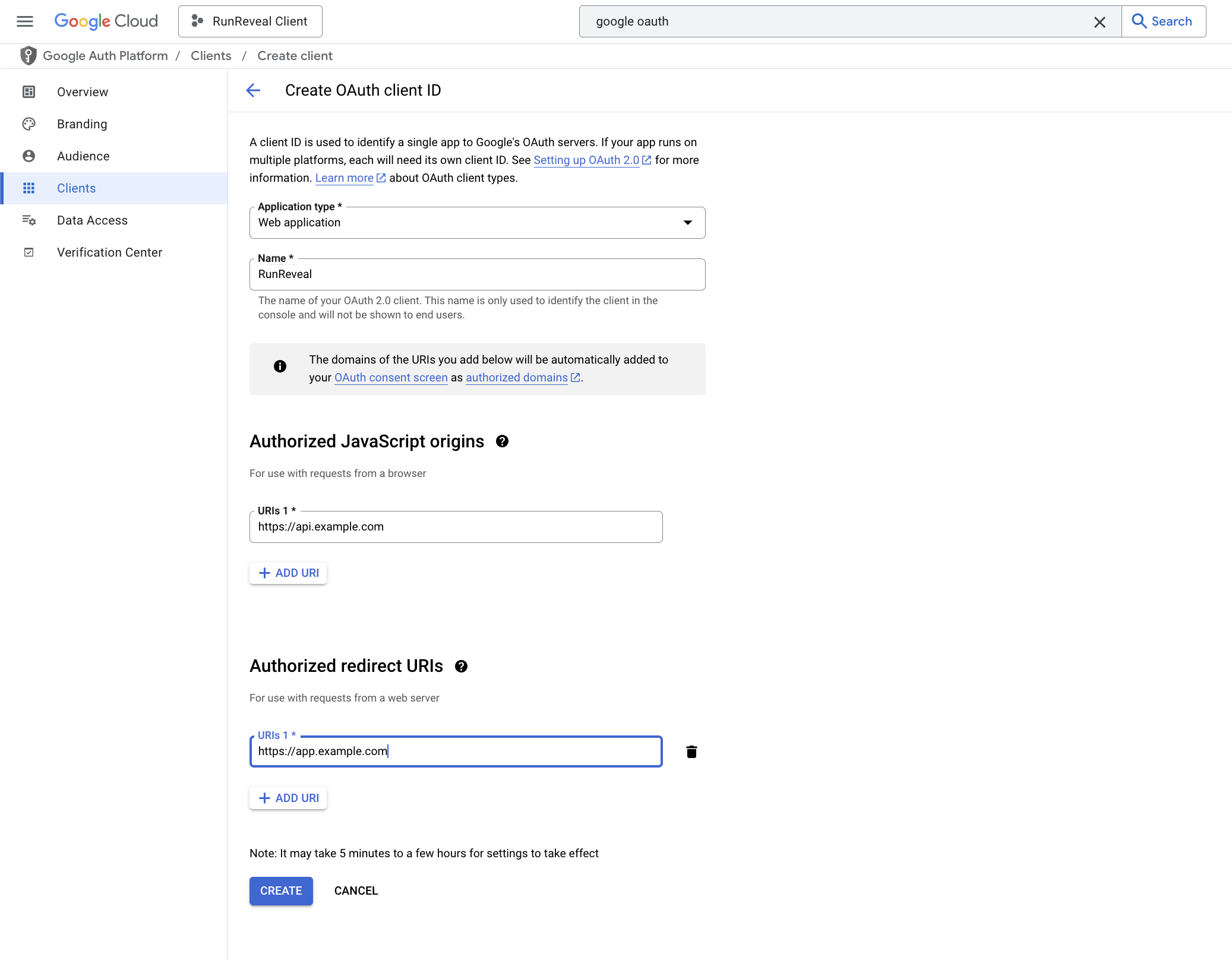
Once you’ve created your project, you’ll need to set the GOOGLE_CLIENT_ID and
GOOGLE_CLIENT_SECRET environment variables when running the api process.