SentinelOne
SentinelOne is an endpoint security platform that uses AI to detect, prevent, and respond to malware, ransomware, and other advanced threats. SentinelOne logs capture endpoint activity such as threat detections, behavioral anomalies, quarantined files, and automated responses taken to mitigate threats. These logs provide valuable insights for monitoring endpoint security, investigating incidents, and ensuring rapid response to cyberattacks.
Ingest Method
This source is a polling source and will download new items from /activities enpoint from the SentinelOne API approximately every 60 seconds.
Setup
Currently the SentinelOne source only supports retrieving items from the /activities api endpoint.
Step 1: Log in to SentinelOne Management Console
- Open your web browser and navigate to your SentinelOne Management Console URL.
- Enter your credentials and click “Sign In”.
Step 2: Access the API Token Generation Page
- Once logged in, click on your user profile icon in the top-right corner of the screen.
- From the dropdown menu, select “My User”.
- In the left sidebar, click on “API Tokens”.
Step 3: Generate a New API Token
- On the API Tokens page, click the “Generate” button.
- You’ll be prompted to enter a name for your API token. Choose a descriptive name that indicates its purpose, for example, “Integration API Key”.
- Select the appropriate scope for this API key. The scope determines what actions the API key can perform. For most integrations, you’ll need at least “Read” permissions.
- Set an expiration date for the token. It’s a good security practice to set an expiration date rather than creating a token that never expires.
- Click “Generate” to create the new API token.
Step 4: RunReveal setup
Create the source in the RunReveal sources dashboard. You will need your organizations SentinelOne domain and the created API key.
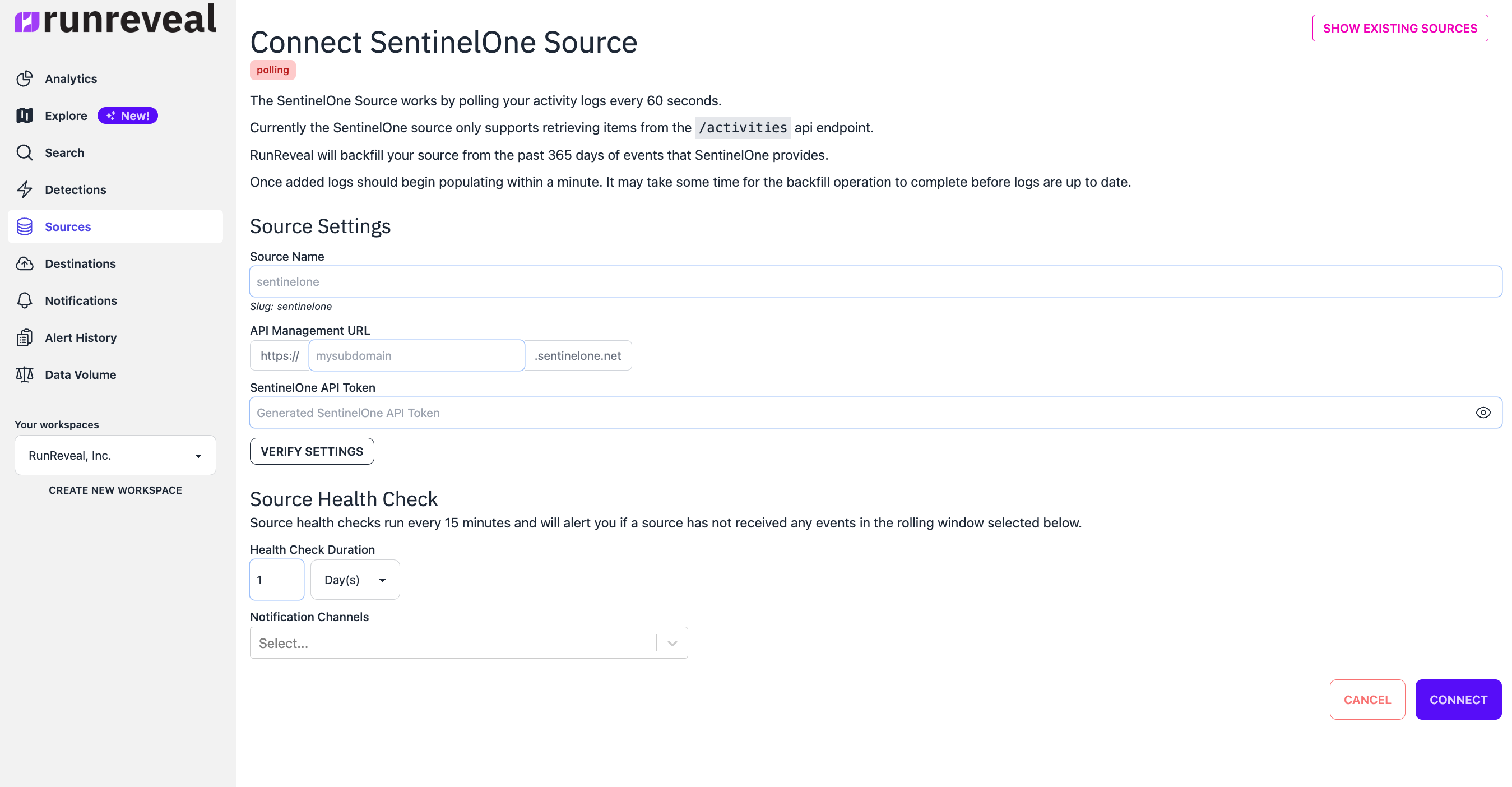
RunReveal will backfill your source from the past 365 days of events that SentinelOne provides.
Once added logs should begin populating within a minute. It may take some time for the backfill operation to complete before logs are up to date.
Schema
The following columns are exposed for this source. RunReveal applies schema normalization across all sources, ensuring uniform field names and data types for cross-source queries and reusable detection logic.
Table: sentinelone_endpoint_logs (149 columns)
sentinelone_endpoint_logs (149 columns)| Column | Type |
|---|---|
workspaceID | String |
sourceID | String |
sourceType | LowCardinality(String) |
sourceTTL | UInt32 |
receivedAt | DateTime |
id | String |
eventName | String |
srcIP | String |
srcASCountryCode | String |
srcASNumber | UInt32 |
srcASOrganization | String |
srcCity | String |
srcConnectionType | String |
srcISP | String |
srcLatitude | Float64 |
srcLongitude | Float64 |
srcUserType | String |
dstIP | String |
dstASCountryCode | String |
dstASNumber | UInt32 |
dstASOrganization | String |
dstCity | String |
dstConnectionType | String |
dstISP | String |
dstLatitude | Float64 |
dstLongitude | Float64 |
dstUserType | String |
actor | Map(String, String) |
tags | Map(String, String) |
resources | Array(String) |
serviceName | String |
enrichments | Array(Tuple(data Map(String, String), name String, provider String, type String, value String)) |
readOnly | Bool |
rawLog | String |
timestamp | String |
dataSourceName | String |
dataSourceVendor | String |
dataSourceCategory | String |
endpointName | String |
endpointOS | String |
endpointType | String |
siteName | String |
siteID | String |
accountName | String |
accountID | String |
agentUUID | String |
agentVersion | String |
mgmtURL | String |
mgmtID | String |
mgmtOSRevision | String |
osName | String |
traceID | String |
packetID | String |
groupID | String |
processUniqueKey | String |
iVersion | String |
iScheme | String |
metaEventName | String |
eventType | String |
eventID | String |
eventCategory | String |
eventTime | UInt64 |
srcProcessName | String |
srcProcessDisplayName | String |
srcProcessUser | String |
srcProcessUserSid | String |
srcProcessUID | String |
srcProcessPID | UInt64 |
srcProcessStartTime | UInt64 |
srcProcessSessionID | UInt64 |
srcProcessCmdline | String |
srcProcessPublisher | String |
srcProcessSignedStatus | String |
srcProcessVerifiedStatus | String |
srcProcessIntegrityLevel | String |
| Column | Type |
|---|---|
srcProcessSubsystem | String |
srcProcessIsNative64Bit | Bool |
srcProcessIsStorylineRoot | Bool |
srcProcessIsRedirectCmdProcessor | Bool |
srcProcessImagePath | String |
srcProcessImageUID | String |
srcProcessImageSize | UInt64 |
srcProcessImageType | String |
srcProcessImageBinaryIsExecutable | Bool |
srcProcessImageMD5 | String |
srcProcessImageSHA1 | String |
srcProcessImageSHA256 | String |
srcProcessParentName | String |
srcProcessParentDisplayName | String |
srcProcessParentUser | String |
srcProcessParentUID | String |
srcProcessParentPID | UInt64 |
srcProcessParentStartTime | UInt64 |
srcProcessParentSessionID | UInt64 |
srcProcessParentCmdline | String |
srcProcessParentPublisher | String |
srcProcessParentSignedStatus | String |
srcProcessParentIntegrityLevel | String |
srcProcessParentSubsystem | String |
srcProcessParentIsNative64Bit | Bool |
srcProcessParentIsStorylineRoot | Bool |
srcProcessParentIsRedirectCmdProcessor | Bool |
srcProcessParentStorylineID | String |
srcProcessParentImagePath | String |
srcProcessParentImageUID | String |
srcProcessParentImageSize | UInt64 |
srcProcessParentImageType | String |
srcProcessParentImageMD5 | String |
srcProcessParentImageSHA1 | String |
srcProcessParentImageSHA256 | String |
srcProcessParentImageSignatureIsValid | Bool |
tgtProcessName | String |
tgtProcessDisplayName | String |
tgtProcessUser | String |
tgtProcessUserSid | String |
tgtProcessUID | String |
tgtProcessPID | UInt64 |
tgtProcessStartTime | UInt64 |
tgtProcessSessionID | UInt64 |
tgtProcessSignedStatus | String |
tgtProcessVerifiedStatus | String |
tgtProcessIntegrityLevel | String |
tgtProcessSubsystem | String |
tgtProcessIsNative64Bit | Bool |
tgtProcessIsStorylineRoot | Bool |
tgtProcessIsRedirectCmdProcessor | Bool |
tgtProcessStorylineID | String |
tgtProcessImagePath | String |
tgtProcessImageUID | String |
tgtProcessImageSize | UInt64 |
tgtProcessImageType | String |
tgtProcessImageBinaryIsExecutable | Bool |
tgtProcessImageMD5 | String |
tgtProcessImageSHA1 | String |
tgtProcessImageSHA256 | String |
tgtProcessPublisher | String |
srcIPAddress | String |
dstIPAddress | String |
srcPortNumber | UInt64 |
dstPortNumber | UInt64 |
eventNetworkDirection | String |
eventNetworkProtocolName | String |
eventNetworkConnectionStatus | String |
eventDNSRequest | String |
eventDNSResponse | String |
eventDNSResponseCode | UInt64 |
eventDNSProtocol | String |
eventDNSProvider | String |
srcProcessStorylineID | String |