Single Sign-On (SSO) Configuration
RunReveal provides Single Sign-On (SSO) capabilities through WorkOS, enabling your organization to authenticate users via your existing identity provider (IdP) using SAML 2.0. This integration allows centralized user authentication while maintaining security compliance requirements and simplifying access management across your security operations team.
SSO implementation in RunReveal focuses on streamlining the authentication process without compromising the platform’s security-first approach. The integration validates users against your organization’s identity provider while preserving RunReveal’s role-based access control (RBAC) system for workspace permissions.
How SSO Works in RunReveal
The SSO authentication flow operates through a SAML-based validation process that connects your identity provider with RunReveal’s authentication system. When a user attempts to sign in with SSO, RunReveal redirects them to your configured identity provider for authentication. Upon successful validation, the identity provider sends a SAML assertion back to RunReveal via WorkOS, confirming the user’s identity and email domain ownership.
This process ensures that authentication remains within your organization’s control while RunReveal handles authorization through its existing workspace and role management system. The separation of authentication (handled by your IdP) and authorization (managed by RunReveal) provides flexibility in user management while maintaining security boundaries.
Prerequisites
Before initiating SSO configuration, ensure your organization meets these requirements:
- Identity Provider: An active SAML 2.0-compatible identity provider (Okta, Azure AD, Google Workspace, OneLogin, or similar)
- Email Domains: Confirmed ownership of the email domains your users will authenticate from
- Admin Access: Administrative privileges in both RunReveal and your identity provider
- User Inventory: A list of users who need RunReveal access with their corresponding roles
Configuration Process
Request SSO Setup
Contact RunReveal support to initiate the SSO configuration process. Provide the complete list of email domains that will use SSO authentication (for example, @yourcompany.com). RunReveal will verify domain ownership and prepare your workspace for SSO integration.
Receive Configuration Link
RunReveal will generate a unique WorkOS configuration link specifically for your organization. This link provides access to the self-service setup portal where you’ll configure the connection between your identity provider and RunReveal.
If your configuration link expires, please let us know and we will generate a new one for you.
Configure Identity Provider
Access the WorkOS configuration portal using your provided link. The portal guides you through configuring your specific identity provider with the necessary SAML endpoints, certificates, and attribute mappings. The configuration interface adapts based on your selected IdP, providing provider-specific instructions and validation steps.
Follow one of the provider-specific configuration guides available at WorkOS SAML integration guides for detailed setup instructions tailored to your identity provider.
User Provisioning
After completing the SSO configuration, you can choose between manual user provisioning or Just-In-Time (JIT) provisioning. With manual provisioning, users must be explicitly invited to the RunReveal workspace before they can access it. Each user requires:
- An invitation to the appropriate RunReveal workspace
- Role assignment according to your security team’s structure (see RBAC documentation)
- Email domain matching your configured SSO domains
For bulk user provisioning, provide RunReveal support with a CSV containing email addresses and their corresponding roles. This accelerates initial deployment for large teams.
Alternatively, you can enable Just-In-Time (JIT) provisioning to automatically create user accounts when users first authenticate via SSO. See the Just-In-Time Provisioning section below for details.
Test Authentication
Verify the SSO configuration by having a test user authenticate through your identity provider. The authentication flow should redirect users from RunReveal’s login page to your IdP, then back to RunReveal upon successful validation. Monitor both systems’ audit logs during testing to ensure proper SAML assertion exchange.
User Management
Adding New Users
New users joining your organization follow different onboarding processes depending on whether JIT provisioning is enabled:
With JIT Provisioning Enabled:
- SSO Authentication: The user authenticates via your identity provider using their corporate email
- Automatic Account Creation: RunReveal automatically creates the user account with the configured default role
- Immediate Access: The user gains immediate access to the workspace
With Manual Provisioning (JIT Disabled):
- Workspace Invitation: An administrator invites the user to the RunReveal workspace with appropriate role assignment
- Email Verification: The user receives an invitation email to their corporate address
- SSO Authentication: Upon accepting the invitation, the user authenticates via your identity provider
- Access Grant: RunReveal validates the SAML assertion and grants workspace access based on the assigned role
Role Assignment
RunReveal maintains its own role-based access control system independent of your identity provider’s groups or roles. This design ensures consistent permission management within the platform while allowing flexibility in your IdP configuration. Administrators must explicitly assign RunReveal roles during user invitation or through subsequent role modifications.
Available roles include:
- Admin: Full administrative control including workspace management and user administration
- Analyst: Detection creation, modification, and analysis capabilities
- Operator: Operational tasks including query execution and report management
- CIBot: Automated system access for CI/CD pipelines and integrations
Custom Roles
In addition to the default roles, RunReveal supports custom roles that provide fine-grained access control by combining UI/API permissions with data-level restrictions.
For detailed information on creating, configuring, and managing custom roles, including UI/API permissions, data access controls, and log filtering options, see the Custom Roles documentation.
For detailed role permissions of default roles, see the Role-Based Access Control documentation.
Just-In-Time (JIT) Provisioning
Just-In-Time (JIT) provisioning automatically creates user accounts in RunReveal when users first authenticate via SSO, eliminating the need for manual user invitations. This feature streamlines user onboarding by allowing users to access RunReveal immediately upon their first SSO login, provided they meet the configured criteria.
How JIT Provisioning Works
When JIT provisioning is enabled, users who authenticate via SSO for the first time are automatically created in the workspace with a default role. The system validates the user’s email domain against your configured SSO domains and creates the account if the domain matches. This process happens seamlessly during the SSO authentication flow, requiring no manual intervention from administrators.
JIT Configuration
SSO vs JIT Scope: SSO is enabled at the organization level, but JIT provisioning settings are configured per workspace. This means if your organization has multiple workspaces, you can enable JIT provisioning on just one workspace, or configure different default roles for each workspace.
If your organization already has SSO configured and working, you can access JIT provisioning settings from the workspace Settings page. On the Settings page, you’ll see your configured SSO domains displayed at the top of the SSO section. The JIT configuration options allow you to:
- Enable or disable JIT provisioning for the workspace
- Set a default role that new users receive when automatically provisioned (can be any role available in the workspace, including custom roles)
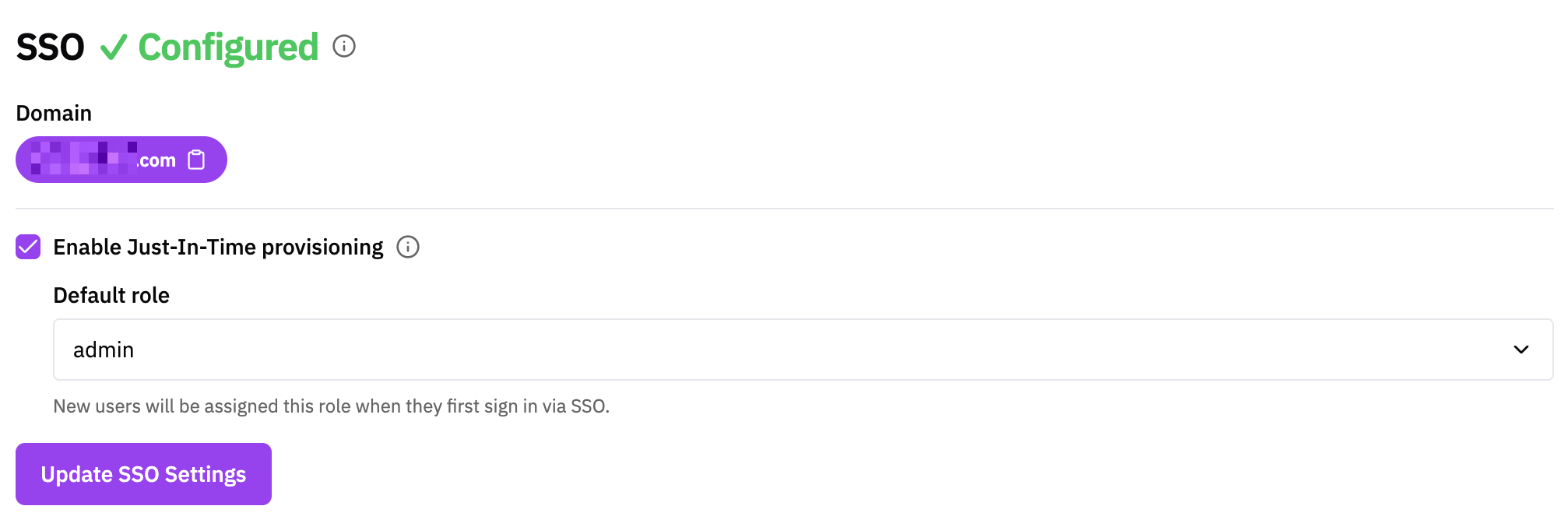
Enabling JIT Provisioning
- Navigate to your workspace Settings page
- Locate the SSO section and review the configured domains (these are set at the organization level)
- Find the Just-In-Time Provisioning section under SSO
- Enable JIT provisioning for the workspace by checking the “Enable Just-In-Time provisioning” checkbox
- Once the checkbox is enabled, a Default role dropdown will appear below it
- Select the default role that new users should receive from the dropdown (this includes all roles available in your workspace, including custom roles)
- Save your configuration
Once enabled, any user who successfully authenticates via SSO with an email domain matching your configured SSO domains will be automatically created in the workspace with the specified default role. The configured SSO domains are displayed in the Settings page so you can verify which email domains are eligible for automatic provisioning.
SCIM Provisioning
SCIM (System for Cross-domain Identity Management) provisioning automates user lifecycle management by synchronizing your identity provider’s directory with RunReveal. Unlike JIT provisioning, which creates accounts at first login, SCIM provisioning responds to changes in your directory in near real-time: when a user is added to your IdP, they are provisioned in RunReveal; when a user is removed from your IdP, they are deprovisioned.
SCIM provisioning requires a connection between your organization’s directory and WorkOS. Contact RunReveal support to enable SCIM for your organization before configuring workspace-level settings.
How SCIM Provisioning Works
RunReveal listens for directory sync events from WorkOS and applies them to your workspaces according to the rules you configure. Two provisioning strategies are available, and they can be used independently or together:
- All Users: Any user added to your identity provider’s directory is automatically provisioned into the workspace. Any user deleted from the directory is deprovisioned.
- Group-based: Only users who are members of specific SCIM groups are provisioned. When a user is added to a mapped group, they are provisioned in the workspace; when they are removed from the group, they are deprovisioned.
SCIM Configuration
SCIM provisioning is configured per workspace from the Settings page, in the same SSO section as JIT provisioning. The settings allow you to independently enable each provisioning strategy and assign roles to provisioned users.
SCIM vs JIT Scope: Like JIT provisioning, SCIM settings are configured per workspace. If your organization has multiple workspaces, you can configure different SCIM rules for each one.
Provision All Users
To automatically provision every user in your connected directory into a workspace:
- Navigate to your workspace Settings page
- Locate the SSO section and scroll to the SCIM Provisioning area
- Enable Provision all users — this will provision any user added to your identity provider’s directory into this workspace
- Select a Default role for newly provisioned users
- Save your configuration by clicking Update SSO Settings
When this option is enabled, users are provisioned as soon as they are added to the directory and deprovisioned (deleted from RunReveal) when they are deleted from the directory.
When using the Provision all users mode, deprovisioning means the account is deleted from RunReveal entirely.
Provision Users by Group
To provision only users who belong to specific SCIM groups, and optionally assign different roles per group:
- Navigate to your workspace Settings page
- Locate the SSO section and scroll to the SCIM Provisioning area
- Enable Provision by group
- Add one or more group mappings — each mapping pairs a SCIM group with a RunReveal role. Users added to that group are provisioned into the workspace with the mapped role; users removed from the group are deprovisioned (i.e., removed from the workspace).
- Save your configuration by clicking Update SSO Settings
Groups must exist in your identity provider and be synced to WorkOS before they appear as options. If a group is not visible, confirm that your IdP’s SCIM connection is active in WorkOS and that the group has been pushed to the directory.
User Deprovisioning
When a user is removed from your identity provider’s directory, RunReveal deletes the user account entirely. When a user is removed from a mapped SCIM group (with group-based provisioning), they are removed from the corresponding workspace. These actions are recorded in RunReveal’s audit logs under the runreveal-audit source type.
Frequently Asked Questions
What are the current limitations of SSO in RunReveal?
The current SSO implementation provides SAML 2.0 authentication with the following characteristics:
- Role Management: Role assignments and modifications occur within RunReveal rather than inheriting from IdP group memberships. SCIM group mappings assign a role at provisioning time, but subsequent role changes must be made in RunReveal.
- Single Domain per Configuration: Each SSO configuration supports one primary email domain; multiple domains require coordination with RunReveal support
How does SSO affect existing user accounts?
Users with existing RunReveal accounts linked to SSO-enabled email domains continue to function normally. Upon SSO activation, these users can authenticate using either their existing credentials or through SSO, though SSO becomes the recommended method for security consistency. Password-based authentication can be disabled upon request after successful SSO deployment.
What happens if our SSO provider experiences an outage?
RunReveal maintains fallback authentication methods for critical access scenarios. Workspace owners can request emergency access procedures from RunReveal support during IdP outages. Consider maintaining a dedicated break-glass account with password authentication for business continuity planning.
How are SSO audit logs accessed?
Authentication events are logged in both your identity provider and RunReveal’s audit system. RunReveal audit logs capture successful and failed login attempts, including SSO-specific metadata. Check Explorer → Logs table for runreveal-audit sourceType to review audit logs. For detailed information on accessing and querying audit logs, see the Audit Logs documentation.
How do we handle contractor or temporary user access?
For users requiring temporary access without adding them to your primary IdP, RunReveal supports hybrid authentication models. These users can be invited with standard email/password authentication while your permanent staff uses SSO. Implement appropriate audit controls and regular access reviews for these exceptions.
Troubleshooting
Common Configuration Issues
When SSO authentication fails, systematically verify each component of the authentication chain:
- Domain Verification: Confirm the user’s email domain matches configured SSO domains exactly (including subdomains if applicable)
- User Invitation Status: Verify the user has an active invitation or existing account in the RunReveal workspace (if JIT provisioning is disabled). If JIT provisioning is enabled, users are automatically created upon first SSO login
- SAML Certificate: Check certificate expiration dates and ensure proper certificate chain validation
- Network Connectivity: Ensure firewall rules permit SAML assertion posts from your IdP to WorkOS endpoints
- IdP Configuration: Ensure you followed the setup instructions from WorkOS, including the appropriate attribute mapping
Support Resources
For SSO configuration assistance or troubleshooting:
- Documentation: WorkOS integration guides
- Audit Logs: Review authentication attempts in both RunReveal and your IdP audit systems
For urgent authentication issues affecting multiple users, contact RunReveal support immediately for priority assistance and potential emergency access activation.
Next Steps
After successful SSO deployment, consider these security enhancements:
- Enable mandatory SSO for all users with corporate email domains
- Implement regular access reviews aligned with your security compliance requirements
- Configure automated alerting for authentication anomalies using RunReveal’s detection capabilities
- Document your SSO configuration and emergency access procedures in your security runbooks