Azure Flow Logs
Previously known as NSG Flow logs, Microsoft deprecated NSG flow logs on June 30, 2025 and plans to retire them on September 30, 2027. In order to migrate to the new Azure Flow (also known as Virtual Net Flow) logs please follow Microsoft’s documentation for migration, https://learn.microsoft.com/en-us/azure/network-watcher/nsg-flow-logs-migrate.
Virtual net flow logs control inbound and outbound traffic to and from Azure resources by defining security rules based on IP address, port, and protocol. Virtual net flow logs capture information about network traffic, including source and destination IP addresses, ports, protocols, and whether traffic was allowed or denied. These logs are useful for monitoring network traffic, troubleshooting connectivity issues, and enhancing network security by detecting suspicious or unauthorized traffic patterns.
Ingest Method
Setup the ingestion of this source using the following guide.
Virtual Net Flow Log Forwarding
With the storage account created you can now setup Virtual net flow logs to export to it.
Follow along with Microsoft’s documentation on the exact steps required to create a new flow log. https://learn.microsoft.com/en-us/azure/network-watcher/vnet-flow-logs-manage?tabs=portal#create-a-flow-log
RunReveal Source
Go to RunReveal and add a new source selecting Azure Flow Logs.
Give the source a name and fill in the remaining fields with the saved values from setup.
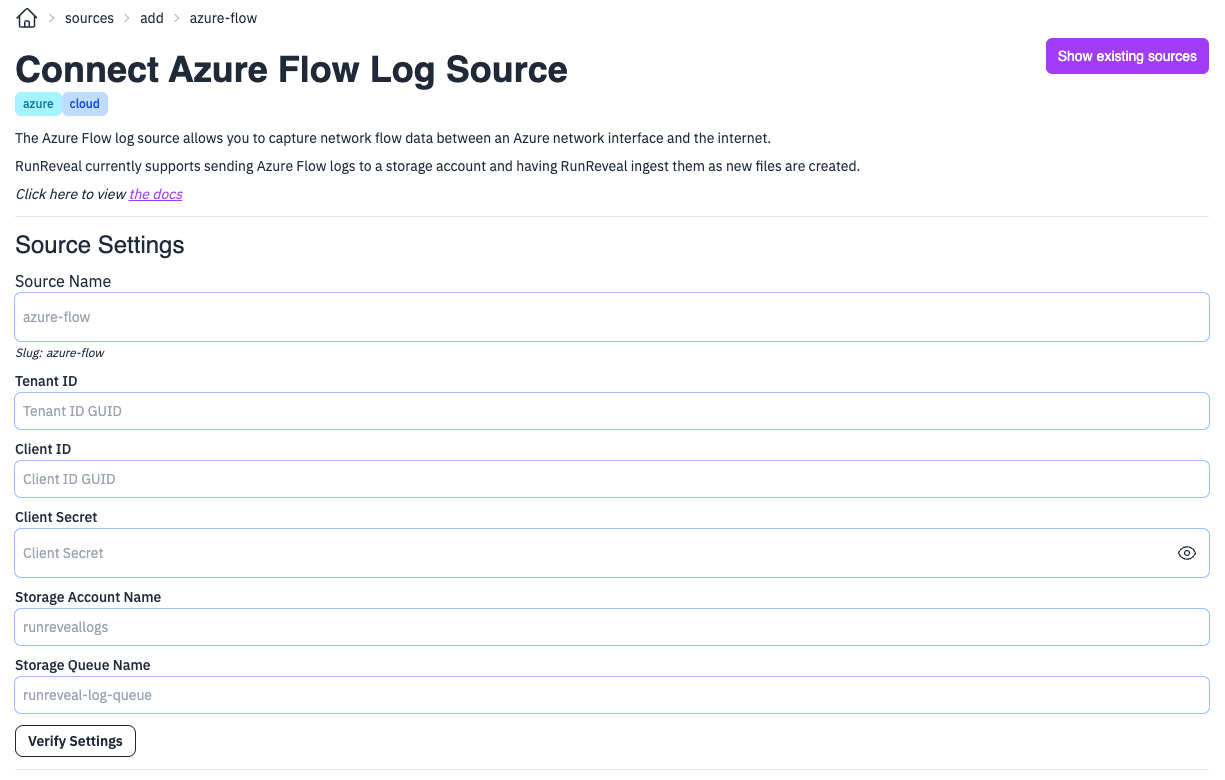
You will need the values that were saved from the setup steps.
- The app
Tenant IDandClient IDfrom the app registration screen. - The
Client Secret Valuethat was created when generating a new secret for the app. - The
Storage Account Namewhere the logs are exporting to. - The
Storage Queue Namethat holds the blob created notifications.
Once these are supplied and saved, RunReveal will begin to process messages in the queue and then ingest logs stored in the bucket.
Because of how Microsoft exports flow logs to storage accounts, logs are usually delayed until the top of the next hour.
Schema
The following columns are exposed for this source. RunReveal applies schema normalization across all sources, ensuring uniform field names and data types for cross-source queries and reusable detection logic.
Table: nsg_flow_logs (50 columns)
nsg_flow_logs (50 columns)| Column | Type |
|---|---|
workspaceID | String |
sourceID | String |
sourceType | LowCardinality(String) |
sourceTTL | UInt32 |
receivedAt | DateTime |
id | String |
eventTime | DateTime |
eventName | String |
eventID | String |
srcIP | String |
srcASCountryCode | String |
srcASNumber | UInt32 |
srcASOrganization | String |
srcCity | String |
srcConnectionType | String |
srcISP | String |
srcLatitude | Float64 |
srcLongitude | Float64 |
srcUserType | String |
dstIP | String |
dstASCountryCode | String |
dstASNumber | UInt32 |
dstASOrganization | String |
dstCity | String |
dstConnectionType | String |
| Column | Type |
|---|---|
dstISP | String |
dstLatitude | Float64 |
dstLongitude | Float64 |
dstUserType | String |
actor | Map(String, String) |
tags | Map(String, String) |
resources | Array(String) |
serviceName | String |
readOnly | Bool |
rawLog | String |
systemID | String |
category | String |
resourceId | String |
operationName | String |
flowVersion | String |
rule | String |
mac | String |
protocol | String |
trafficFlow | String |
trafficDecision | String |
flowState | String |
packetsSent | Int64 |
bytesSent | String |
packetsReceived | Int64 |
bytesReceived | String |
Table: azure_flow_logs (54 columns)
azure_flow_logs (54 columns)| Column | Type |
|---|---|
workspaceID | String |
sourceID | String |
sourceType | LowCardinality(String) |
sourceTTL | UInt32 |
receivedAt | DateTime |
id | String |
eventTime | DateTime |
eventName | String |
eventID | String |
srcIP | String |
srcASCountryCode | String |
srcASNumber | UInt32 |
srcASOrganization | String |
srcCity | String |
srcConnectionType | String |
srcISP | String |
srcLatitude | Float64 |
srcLongitude | Float64 |
srcUserType | String |
dstIP | String |
dstASCountryCode | String |
dstASNumber | UInt32 |
dstASOrganization | String |
dstCity | String |
dstConnectionType | String |
dstISP | String |
dstLatitude | Float64 |
| Column | Type |
|---|---|
dstLongitude | Float64 |
dstUserType | String |
actor | Map(String, String) |
tags | Map(String, String) |
resources | Array(String) |
serviceName | String |
enrichments | Array(Tuple(data Map(String, String), name String, provider String, type String, value String)) |
readOnly | Bool |
rawLog | String |
flowLogGUID | String |
category | String |
flowLogResourceID | String |
targetResourceID | String |
operationName | String |
rule | String |
macAddress | String |
aclID | String |
srcPort | Int |
dstPort | Int |
protocol | Int |
flowDirection | Unknown |
flowState | Unknown |
flowEncryption | String |
packetsSent | Int |
bytesSent | Int |
packetsReceived | Int |
bytesReceived | Int |