Jamf Protect Security Event Forwarding with a Webhook
This guide explains how to configure Jamf Protect Cloud to forward analytic and security events (e.g., screenshot detection, prevented execution, Gatekeeper blocks) to RunReveal using a webhook URL generated in the RunReveal UI.
Prerequisites
- Jamf Protect Cloud admin access
You need rights to configure action configurations and data endpoints. - RunReveal account with permissions to add sources and view logs (admin/editor)
Ability to add sources and view logs. - Configured Jamf Protect analytics
Ensure Jamf Protect is already generating events (e.g., screenshot captures, execution blocks, policy violations).
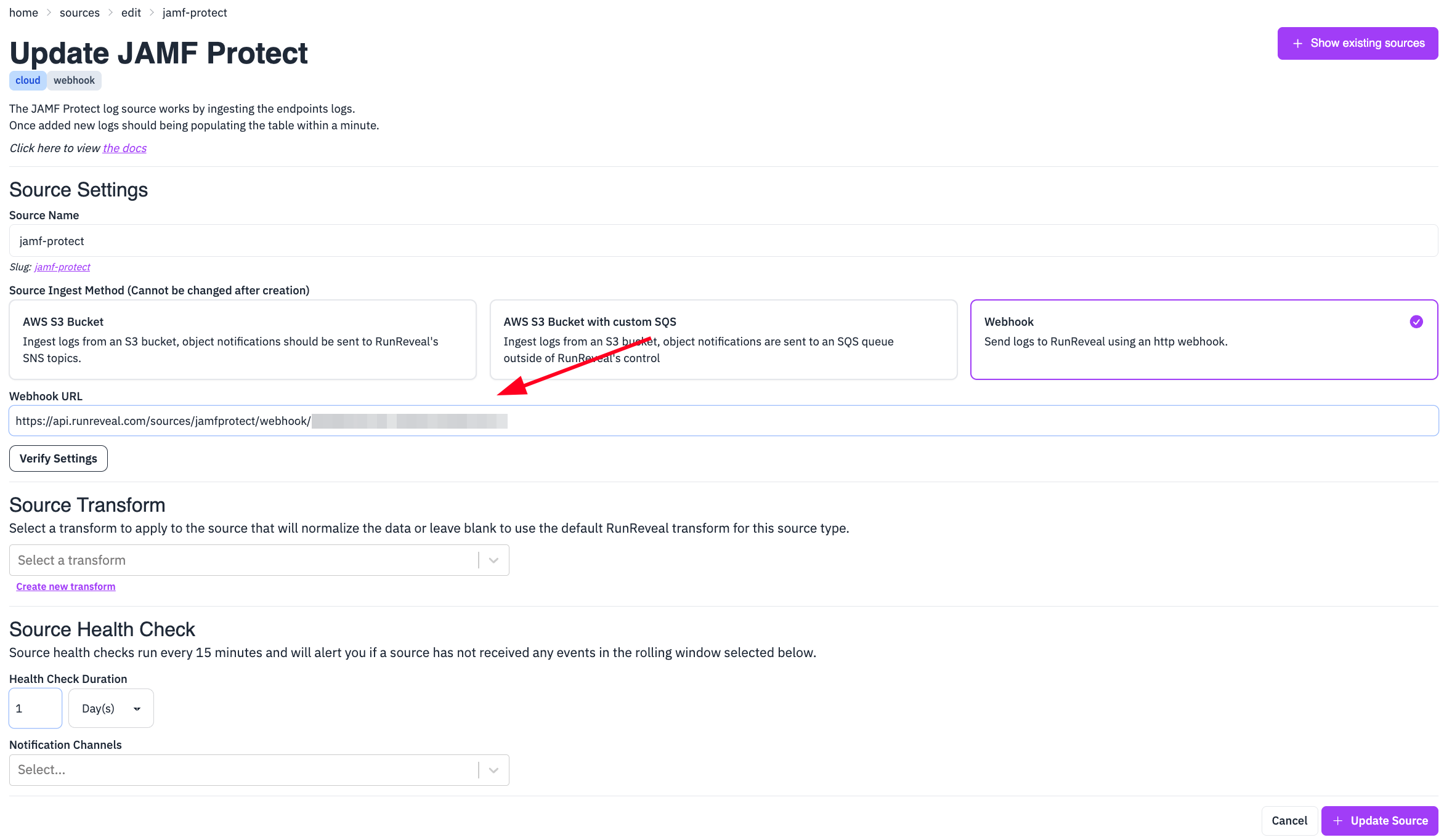
Step 1: Generate a Webhook Endpoint in RunReveal
- Navigate to Sources in RunReveal
- Click Add Source
- Select Jamf Protect and choose Webhook as the ingest type
- Save the source with a descriptive name to generate the unique webhook URL
- Copy the webhook endpoint URL provided
Step 2: Create Data Endpoint Action in Jamf Protect Cloud
- Log in to Jamf Protect Cloud Console
- Navigate to Settings → Action Configurations
- Click New to create a new action configuration
- Select Data Endpoint as the action type
- Provide a descriptive name (e.g., “RunReveal Webhook”)
- Configure the data endpoint settings:
- Endpoint URL: Paste the RunReveal webhook URL you copied earlier
- Method: POST
- Headers: Set Content-Type to application/json
- Authentication: None (authentication handled via the unique webhook URL)
- Data Format: JSON
For more details, see the Creating an Action Configuration - JAMF macOS Security Portal.
Step 3: Select Analytic & Event Types to Forward
- In Jamf Protect, you can attach your Data Endpoint Action to specific analytics or groups of analytics.
- Common event types include:
GPScreenshotEvent(screen capture / MITRE T1113)GPGatekeeperEvent(Gatekeeper enforcement)GPPreventedExecutionEvent(execution blocked)GPThreatMatchExecEvent(analytic match on process execution)
- You can update your configuration later as monitoring needs evolve.
Security Event Type logs format:
{
"caid": "CAID_HASH",
"certid": "CERT_ID_HASH",
"input": {
"eventType": "GPScreenshotEvent",
"host": {
"hostname": "HOST_NAME",
"ips": ["192.0.2.1"],
"os": "Version 15.4.1 (Build 24E263)",
"protectVersion": "7.0.0.9",
"provisioningUDID": "UDID_VALUE",
"serial": "SERIAL_NUMBER"
},
"match": {
"event": {
"path": "/Users/user/Documents/Screenshots/Screenshot 2025-05-12 at 11.15.48 AM (2).png",
"timestamp": 1747062957.09414,
"uuid": "EVENT_UUID"
},
"tags": ["MITREattack", "T1113", "ScreenCapture", "Collection"],
"uuid": "MATCH_UUID"
},
"related": {
"users": [{
"name": "user",
"uid": 501,
"uuid": "USER_UUID_1"
}]
}
}
}Step 4: Validate Delivery
- Return to RunReveal and open your Jamf Protect Source page
- Confirm that events are arriving
- Search in Explorer or use Native AI Chat to inspect recent Jamf Protect analytic events
Schema
The following columns are exposed for this source. RunReveal applies schema normalization across all sources, ensuring uniform field names and data types for cross-source queries and reusable detection logic.
Table: jamf_protect_webhook_logs (73 columns)
jamf_protect_webhook_logs (73 columns)| Column | Type |
|---|---|
id | String |
workspaceID | String |
sourceID | String |
sourceType | String |
sourceTTL | UInt32 |
receivedAt | DateTime64(3) |
eventTime | DateTime64(3) |
eventName | String |
eventID | String |
srcIP | String |
srcASCountryCode | String |
srcASNumber | UInt32 |
srcASOrganization | String |
srcCity | String |
srcConnectionType | String |
srcISP | String |
srcLatitude | Float64 |
srcLongitude | Float64 |
srcUserType | String |
dstIP | String |
dstASCountryCode | String |
dstASNumber | UInt32 |
dstASOrganization | String |
dstCity | String |
dstConnectionType | String |
dstISP | String |
dstLatitude | Float64 |
dstLongitude | Float64 |
dstUserType | String |
actorID | String |
username | String |
hostname | String |
rawLog | String |
hostOS | String |
protectVersion | String |
provisioningUDID | String |
serial | String |
| Column | Type |
|---|---|
actionType | Int32 |
eventType | Int32 |
globalSeqNum | Int64 |
machTime | Int64 |
seqNum | Int64 |
version | Int32 |
timestamp | Int64 |
timestampReceivedISO | String |
processPath | String |
processPid | Int32 |
processUsername | String |
processSigningId | String |
processCdHash | String |
processExecutablePath | String |
processExecutableSha1 | String |
processExecutableSha256 | String |
execArgs | Array(String) |
execDyldPath | String |
execTargetPath | String |
execTargetPid | Int32 |
execTargetUsername | String |
execTargetSigningId | String |
parentProcessPath | String |
parentProcessPid | Int32 |
parentProcessSigningId | String |
responsibleProcessPath | String |
responsibleProcessPid | Int32 |
responsibleProcessSigningId | String |
threadId | Int64 |
threadUUID | String |
clientId | String |
hd | String |
certId | String |
metadataProduct | String |
metadataSchemaVersion | String |
metadataVendor | String |
Troubleshooting
- No events appearing in RunReveal
- Check that your Jamf Protect Data Endpoint action is enabled and pointing to the correct RunReveal URL
- Validate that Jamf Protect analytics are enabled and triggering events
- Use a cURL test with sample JSON to confirm that your webhook URL accepts data