Model Context Protocol
The Model Context Protocol (MCP) allows you to connect AI assistants like Claude and Cursor to external data sources and tools. This guide shows you how to set up RunReveal’s MCP server with both Claude and Cursor.
MCP Setup
RunReveal supports two MCP setup approaches, each designed for different deployment scenarios and authentication preferences:
Remote MCP connects to RunReveal’s hosted MCP server over HTTP/HTTPS, providing a seamless OAuth-based authentication experience. This approach is ideal for most users with hosted RunReveal deployments who want quick setup and don’t need to manage local processes.
Local MCP runs the RunReveal MCP server as a local process using the runreveal mcp command, with API token authentication. This approach is essential for on-premises deployments, air-gapped environments, or when you need fine-grained control over the MCP server process.
Remote MCP
Remote MCP allows you to connect to RunReveal’s hosted MCP server over HTTP/HTTPS. This enables you to:
- Access your RunReveal data and tools from any AI assistant that supports MCP
- Share MCP servers across multiple team members
- Run MCP servers in production environments
- Centralize data access and permissions
- Use OAuth authentication for seamless setup
Setup
Prerequisites:
- A RunReveal account with API access
- Claude Desktop or Claude.ai account
Step 1: Add the Integration
- In Claude, go to Add integration (BETA)
- Enter the following details:
- Integration Name: RunReveal
- Server URL:
https://api.runreveal.com/mcp
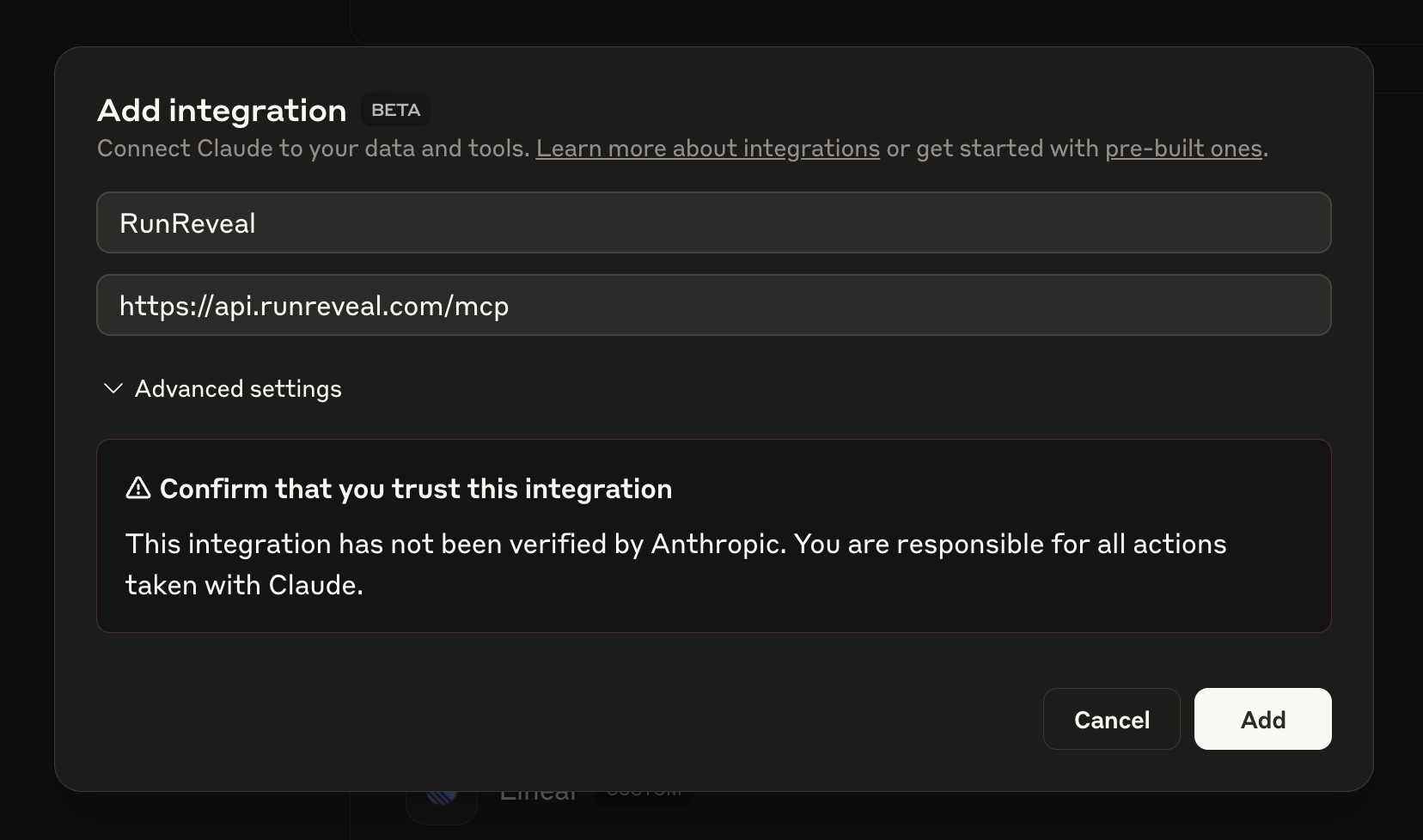
Step 2: Trust the Integration
Claude will show a warning that this integration has not been verified by Anthropic. Click Add to proceed.
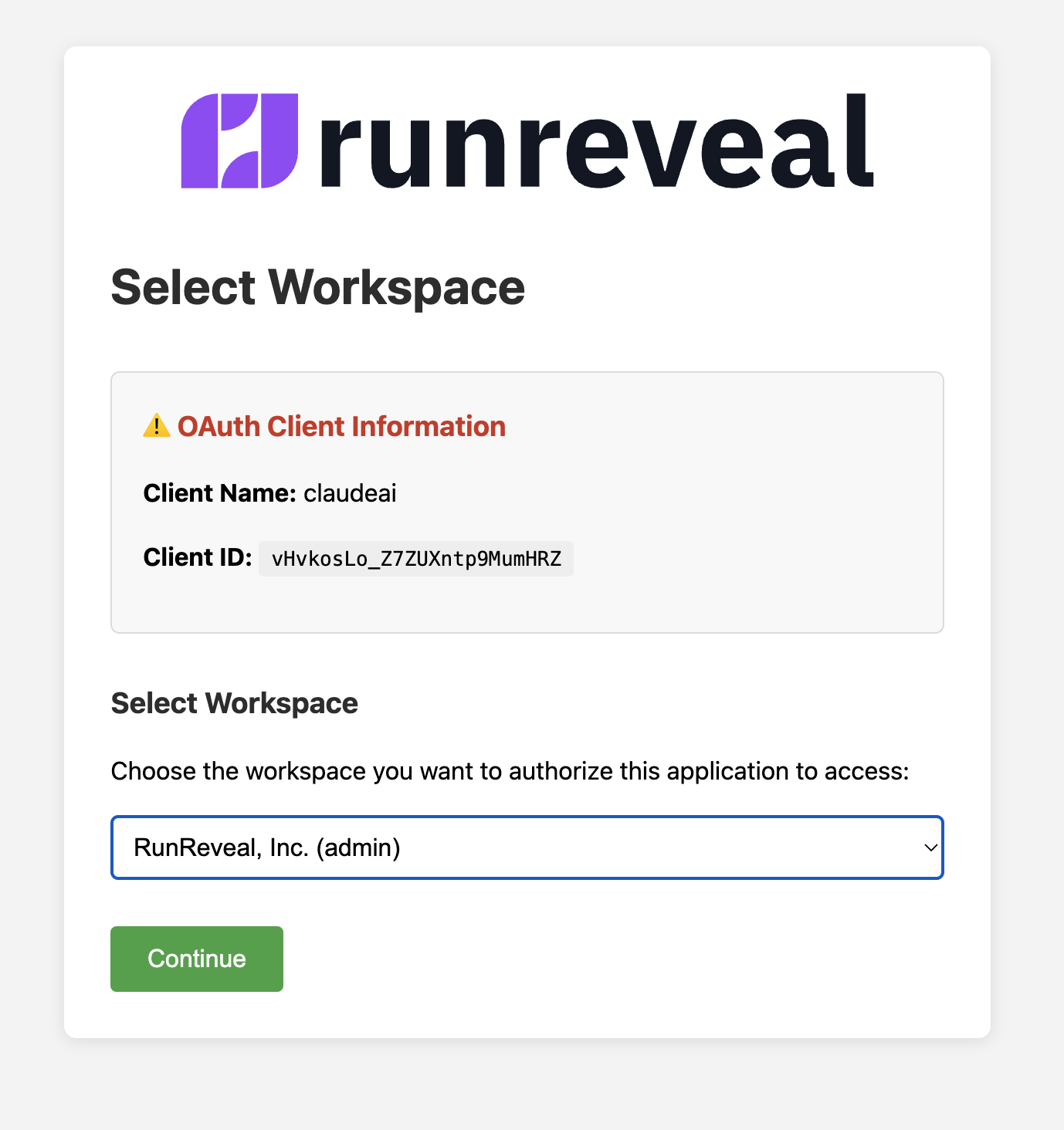
Step 3: Authorize with RunReveal
- You’ll be redirected to RunReveal’s authorization page
- Review the OAuth client information:
- Client Name: claudeai
- Client ID: (will be displayed)
- Select your workspace from the dropdown
- Click Continue to authorize the connection
Alternative: Using Claude Code CLI
If you’re using Claude Code (the CLI tool), you can add the RunReveal MCP server directly from the command line:
claude mcp add -t http runreveal 'https://api.runreveal.com/mcp'This command will:
- Add the RunReveal MCP server to your Claude Code configuration
- Use the identifier “runreveal” for the server
After running this command, the MCP server will be available in your Claude Code sessions, and you’ll go through the same OAuth authorization flow when first accessing RunReveal tools.
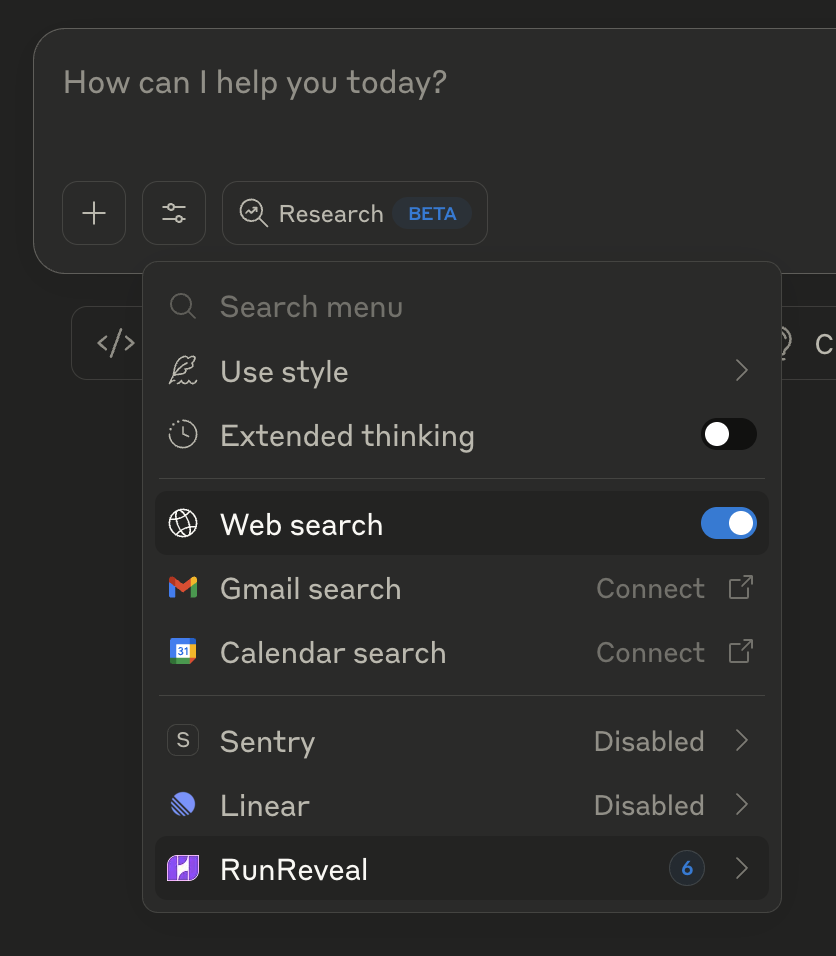
Step 4: Verify the Connection
Once authorized, you should see RunReveal listed in your Claude integrations with available tools:
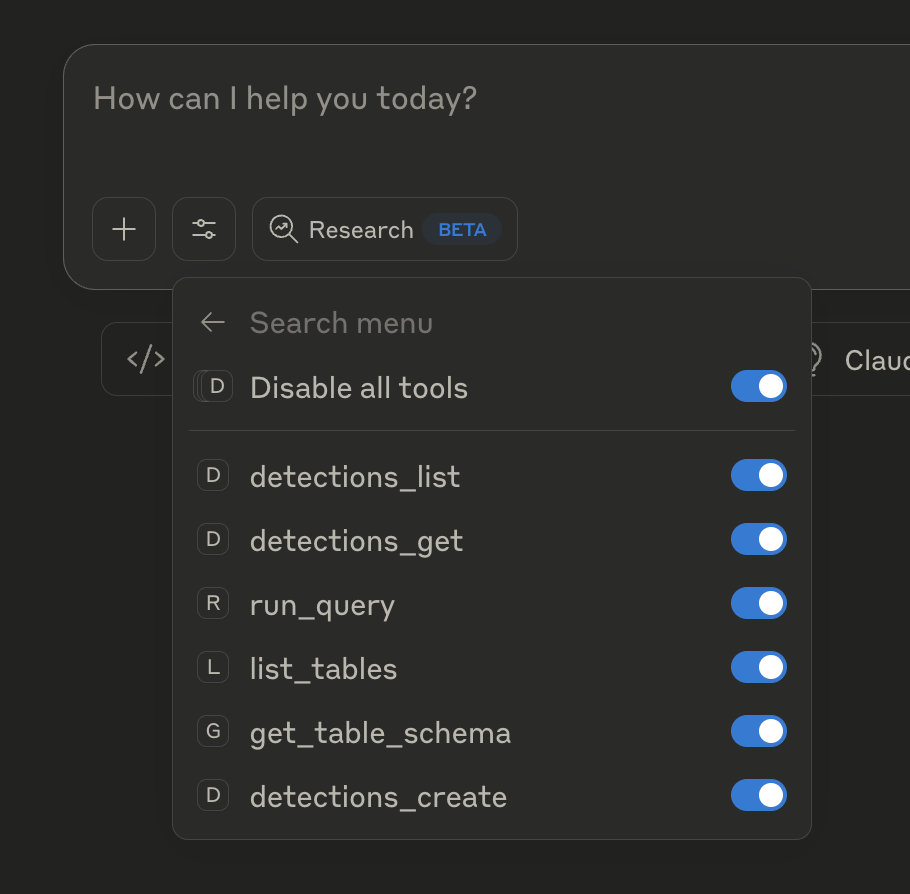
Available Tools
The RunReveal MCP integration provides access to the following tools. Each tool requires the listed permission (OAuth scope or API token scope) in your workspace.
| Tool | What it does | Permission |
|---|---|---|
source_list | List available data sources (optional filter by type). | Sources (read) |
run_query | Execute ClickHouse SQL against your log data. Use for exploration, validation, and ad-hoc analysis. Filter by receivedAt and use small limits for performance. | Queries (read) |
list_tables | List available data tables in the workspace. | Queries (read) |
get_table_schema | Get schema and indexes for a table (columns, types, primary key). Use before writing querys. | Queries (read) |
detections_list | List all detection rules with optional filters (severity, category, type, etc.). | Queries (read) |
detections_get | Get full details for a single detection by name. | Queries (read) |
detections_create | Create a new SQL detection (query, schedule, metadata). Requires user confirmation before use. | Queries (edit) |
detection_update | Update an existing detection rule. Requires user confirmation before use. | Queries (edit) |
detection_delete | Delete a detection rule. Requires user confirmation before use. | Queries (edit) |
notification_list | List notification channels configured for the workspace. | Notifications (read) |
notification_send | Send a notification to one or more channels (template or inline title/body). | Notifications (edit) |
investigation_list | List investigations with optional filters (status, severity, tags). | Investigations (read) |
investigation_get | Get a single investigation by ID or name, including artifacts and timeline. | Investigations (read) |
All currently available tools require appropriate OAuth scopes for your workspace.
The detections_create tool requires write permissions, while other tools require read permissions.
OAuth tokens are workspace-specific and use scopes rather than traditional roles.
Example Usage
Once set up, you can ask your AI assistant real questions like these. Each type of use case can use multiple MCP tools (e.g. list_tables, get_table_schema, run_query) to answer.
- ”Show me failed logins in the last 24 hours."
- "What tables do we have? Show me the schema for the auth table."
- "List our data sources."
- "Sample the last 10 rows from our CrowdStrike FDR logs."
- "Which event types appear most in our logs this week?"
- "How many events did we receive per hour yesterday?"
Writing detections with Cursor and Claude MCP
Connect RunReveal MCP in Cursor or Claude and add the detection guide below to your AI’s rules or instructions. The AI can then use your schema and logs to review and create detections from real data. You can also build and refine detections in RunReveal’s in-app chat; see Native AI Chat for more.
- Connect RunReveal MCP (Remote or Local) as described above in this page.
- Add the detection guide to Cursor rules so the AI follows best practices: open Cursor Settings → Rules (or create a
.cursor/rulesfile in your repo), create a rule (e.g. RunReveal detection writing) and paste the contents of the Detection Engineering Guide from the expandable block below. - Use the AI to write or refine detections: ask in natural language (e.g. create a detection for suspicious failed logins from the same IP in the last 15 minutes). The AI can call
get_table_schemaandrun_query, thendetections_create. - Review before enabling: check the generated detection in the RunReveal UI and enable notifications/severity as needed.
Detection Engineering Guide (copy into Cursor rules or Claude instructions)
Field names and validation in this guide match the RunReveal app and API: app (app/src/validation/detectionSchemas.ts) and API (api/models/api.go, e.g. DetectionSyncRequest for SQL; Sigma parsing in api/detections.go). Treat those as the source of truth for casing and allowed values.
Expand: Full detection writing guide to copy into Cursor rules or Claude custom instructions
Copy the markdown below into a Cursor rule or into Claude’s custom instructions so the AI follows RunReveal detection best practices when using MCP tools.
# RunReveal Detection Engineering Guide
Best practices for SQL scheduled detections, Sigma real-time rules, and validation. **Always validate against actual log data first—never assume schemas or field names.**
## Detection Type Selection
**SQL (scheduled):** Batch analysis, aggregations, cross-source correlation, historical patterns. Requires `{from:DateTime}` and `{to:DateTime}`; schedule via cron (e.g. `*/15 * * * *`). Order WHERE by primary key; use indexed columns (`get_table_schema`). Default 15-min; use 5-min for near-real-time. If Sigma fails, deploy as SQL with 5-min schedule.
**Sigma (real-time):** Single-event pattern matching, sub-minute alerting. Create via RunReveal UI only (not MCP/API). Parser may not support all Sigma operators.
## Pre-Detection Validation (MANDATORY)
Before writing any detection:
1. **Schema** — Get table schema (columns, types, indexes, primary key).
2. **Sample data** — `SELECT * FROM target_table WHERE receivedAt >= now() - INTERVAL 7 DAY ORDER BY receivedAt DESC LIMIT 5` to confirm field names and values (case-sensitive).
3. **Event distribution** — `SELECT eventName, count() FROM target_table WHERE receivedAt >= now() - INTERVAL 7 DAY GROUP BY eventName ORDER BY cnt DESC LIMIT 20` to confirm relevant event types exist.
4. **Platform** — Group by platform/env to avoid Windows-only detections in Mac-only environments.
5. **Test logic** — Run detection WHERE clause with `LIMIT 5`; confirm field access works and execution time <1500ms.
6. **Document** — Platform, event types, data volume, limitations (e.g. "Mac only, no Windows—PowerShell N/A").
## Field Usage
Use **normalized columns** when available (indexed, faster). Use JSON extraction only when the field is not a table column. Check schema first.
- Prefer: `WHERE ImageFileName = '/bin/bash' AND CommandLine LIKE '%curl%' AND eventName = 'ProcessCreate'`
- JSON only when not normalized: `JSONExtractString(rawLog, 'ComputerName') AS ComputerName`
## SQL Detection Creation
**Template:** Always time-bound with `{from:DateTime}` / `{to:DateTime}`. Select from your table with `receivedAt >= {from:DateTime} AND receivedAt < {to:DateTime}` plus indexed fields first, then detection logic. Order WHERE by primary key for partition pruning.
**Rules:** (1) Use indexed fields early; avoid functions on them. (2) Targets: 15-min <1000ms, 1-hour <2000ms.
**ClickHouse:** Maps `map['key']`, `actor['email']`. JSON: `JSONExtractString(rawLog,'key')`, `JSONExtractInt`, `JSONExtractBool`; nested: `JSONExtractString(rawLog,'p','c')`. Use `count()` not `count(*)`. Arrays: `has(arr,'val')`, `arrayExists(x->x='val',arr)`.
## Naming
- **Display name:** Clear, human-readable (e.g. *Suspicious Shell Script Execution*).
- **Name (slug):** Alphanumeric and hyphens only, 3–128 chars, lowercase (e.g. `suspicious-shell-script-execution`). No underscores or spaces.
## MITRE ATT&CK
- **mitreAttacks:** `TA####` only (e.g. `TA0001`). Pattern: `^TA\d{4}$`.
- **mitreTechniques:** `T####` or `T####.###` (e.g. `T1078`, `T1136.001`). Sub-technique must be 3 digits. Invalid IDs (e.g. `t1078`, `T1136.1`) are rejected.
- Example: `mitreAttacks: [TA0001, TA0005]` and `mitreTechniques: [T1078, T1059.004]`.
- **Sigma YAML:** Use `level` for severity (not `severity`); use lowercase `riskscore` and `notificationnames`. `mitreAttacks` and `mitreTechniques` stay camelCase.
## Testing Checklist
Before deploy: data validated (real logs), platform verified, `query` tested (expected or zero results), execution time <1500ms, exclusions for known-good tools, field access validated, MITRE mapped, severity and notifications set.
## Pitfalls
**Don't:** Create without checking logs; use platform-specific rules for wrong env; skip performance test; assume zero results = broken detection.
**Do:** Run schema + sample + event-distribution `query`s; test WHERE with LIMIT; document platform and limitations; add exclusions and investigation guidance.
## SQL vs Sigma
**SQL:** Aggregations, cross-source, complex logic, or when Sigma fails (use 5-min SQL). **Sigma:** Single-event pattern, sub-minute alerting. Default to SQL with 5-min unless sub-minute is required.
## Investigation Fields
Include where available: user (username, email), system (hostname, srcIP, dstIP), event (name/type, time, ID), process (name, command line, PID, parent), resource (name, type, ID). Use actual source field names; alias for clarity.Example: CrowdStrike FDR logs and Sigma rules for MITRE coverage
This simple example prompt was run against CrowdStrike FDR logs in a test workspace and produced the response in the expandable block below.
Example prompt: “review our crowdstrike fdr logs and suggest a sigma rule to create for mitre coverage”
Expand: Example response: (Sigma Rule)
The following is an example of the kind of output you can get when the AI uses the detection guide and MCP tools to analyze your logs and suggest detections.
Recommended Sigma Rules
1. Suspicious Script Execution from Temporary Directories (Defense Evasion: T1027)
Detection Goal: Identify scripts (shell, Python, Perl) executed from temporary or user-writable directories, often used by adversaries to avoid persistence detection.
Sigma Rule:
title: Suspicious Script Execution from Temporary Directory
id: crowdstrike-temp-script-exec-001
status: experimental
description: Detects execution of shell scripts or interpreters from temporary directories which may indicate obfuscated files or malicious payloads
logsource:
product: crowdstrike
service: fdr
detection:
selection:
event_simpleName: 'ProcessRollup2'
ImageFileName|contains:
- '/tmp/'
- '/var/tmp/'
- '/dev/shm/'
- '/private/tmp/'
- '/private/var/tmp/'
ImageFileName|endswith:
- '/bash'
- '/sh'
- '/zsh'
- '/python'
- '/python3'
- '/perl'
- '/ruby'
filter_legit:
ParentBaseFileName:
- 'installer'
- 'softwareupdate'
- 'com.apple.installer'
condition: selection and not filter_legit
falsepositives:
- Legitimate software installation processes
- System update mechanisms
- Development environments with frequent script execution
level: medium
tags:
- attack.defense_evasion
- attack.t1027
- attack.t1059.004
mitreAttacks: [TA0005]
mitreTechniques: [T1027.001, T1059.004]
riskscore: 50
2. Unexpected Executable Written to Non-Standard Location (Defense Evasion: T1564.001)
Detection Goal: Detect new executables written to unusual paths (user directories, hidden folders, or non-standard system locations) that adversaries use to hide files.
Sigma Rule:
title: Executable Written to Non-Standard Location
id: crowdstrike-unusual-exec-write-001
status: experimental
description: Detects new executable files written to non-standard locations that may indicate defense evasion through file hiding
logsource:
product: crowdstrike
service: fdr
detection:
selection_event:
event_simpleName: 'NewExecutableWritten'
selection_paths:
TargetFileName|contains:
- '/Users/'
- '/tmp/'
- '/var/tmp/'
- '/.config/'
- '/.local/'
- '/Library/Application Support/'
- '/private/tmp/'
filter_development:
ContextBaseFileName:
- 'xcodebuild'
- 'clang'
- 'gcc'
- 'cmake'
- 'cargo'
- 'go'
filter_installers:
TargetFileName|contains:
- 'Install'
- '.app/Contents/'
condition: selection_event and selection_paths and not filter_development and not filter_installers
falsepositives:
- Software development and compilation activities
- Application installation processes
- Build systems and CI/CD pipelines
level: medium
tags:
- attack.defense_evasion
- attack.t1564.001
- attack.persistence
- attack.t1543
mitreAttacks: [TA0005, TA0003]
mitreTechniques: [T1564.001, T1543.001]
riskscore: 55
3. CrowdStrike API Access from Unexpected IP Addresses (Initial Access: T1078.004)
Detection Goal: Detect CrowdStrike API authentication from IPs outside expected organizational ranges, potentially indicating compromised API credentials or unauthorized access.
Sigma Rule:
title: CrowdStrike API Access from Unexpected Geographic Location
id: crowdstrike-api-suspicious-geo-001
status: experimental
description: Detects CrowdStrike API authentication events from unexpected countries or IP ranges that may indicate compromised credentials
logsource:
product: crowdstrike
service: event_logs
detection:
selection_auth:
eventName: 'APIActivityAuditEvent'
requestPath: '/oauth2/token'
statusCode: '201'
filter_expected_locations:
srcASCountryCode:
- 'US'
- 'CA'
condition: selection_auth and not filter_expected_locations
falsepositives:
- Legitimate access from cloud infrastructure (AWS, GCP, Azure) in various regions
- Remote work from international locations
- Third-party integration vendors
level: high
tags:
- attack.initial_access
- attack.t1078.004
- attack.credential_access
- attack.t1110
mitreAttacks: [TA0001, TA0006]
mitreTechniques: [T1078.004, T1110.001]
riskscore: 75
Implementation Guidance
Pre-Deployment Validation
Before creating these rules in RunReveal, validate event coverage:
-- Verify ProcessRollup2 events with suspicious paths
SELECT event_simpleName, ImageFileName, CommandLine, ParentBaseFileName, count() as cnt
FROM crowdstrike_data_logs
WHERE receivedAt >= now() - INTERVAL 7 DAY AND event_simpleName = 'ProcessRollup2'
AND (ImageFileName LIKE '%/tmp/%' OR ImageFileName LIKE '%/var/tmp/%')
GROUP BY event_simpleName, ImageFileName, CommandLine, ParentBaseFileName
ORDER BY cnt DESC LIMIT 20;
-- Verify NewExecutableWritten events
SELECT JSONExtractString(rawLog, 'TargetFileName') as target_file, JSONExtractString(rawLog, 'ContextBaseFileName') as context_process, count() as cnt
FROM crowdstrike_data_logs
WHERE receivedAt >= now() - INTERVAL 7 DAY AND event_simpleName = 'NewExecutableWritten'
GROUP BY target_file, context_process ORDER BY cnt DESC LIMIT 20;
-- Verify API authentication events
SELECT requestPath, statusCode, srcASCountryCode, srcIP, count() as cnt
FROM crowdstrike_event_logs
WHERE receivedAt >= now() - INTERVAL 7 DAY AND eventName = 'APIActivityAuditEvent' AND requestPath = '/oauth2/token'
GROUP BY requestPath, statusCode, srcASCountryCode, srcIP ORDER BY cnt DESC;
Expected MITRE Coverage Impact
These three rules will provide coverage for:
Defense Evasion (TA0005): T1027.001, T1564.001
Execution (TA0002): T1059.004
Persistence (TA0003): T1543.001
Initial Access (TA0001): T1078.004
Credential Access (TA0006): T1110.001
This represents 5 tactics and 7 techniques, establishing a strong detection foundation for CrowdStrike telemetry.
Next Steps
Create rules via RunReveal UI: Navigate to Detections → Create Detection → Select Sigma format
Tune filters: Adjust country codes in Rule #3 and path exclusions in Rules #1-2 based on organizational baselines
Set notification channels: Configure Slack, email, or webhook notifications per rule severity
Monitor for 48-72 hours: Collect signal data before enabling alerting to reduce false positives
Document investigation workflows: Create runbooks for each rule with escalation criteria
For additional Defense Evasion coverage (process injection, DLL side-loading, masquerading), reference CrowdStrike's event catalog at https://falcon.crowdstrike.com/documentation/86/event-explorer.Troubleshooting
If tools fail or you see permission errors:
- Verify your RunReveal user/token has appropriate OAuth scopes (or API token permissions) for the tools you’re using.
- OAuth tokens are workspace-specific and use scopes rather than traditional roles.
- For local MCP, ensure your API token has the necessary permissions for the tools you plan to use.
- The
detections_create,detection_update, anddetection_deletetools require write (edit) permissions; most others require read.
Related Documentation
Now that you have MCP set up, explore these related guides:
- Agents - Automate AI-powered agents to run on a schedule and analyze your data
- Native AI Chat - Interactive AI-powered investigations in RunReveal
- Prompts - Create reusable prompt templates with arguments
- Detections - Create and manage detection rules
- Notifications - Set up alerting and notification channels
- Investigations - Manage and track security investigations