Native AI Chat
RunReveal’s Native AI Chat is a purpose-built investigation agent that lets you analyze your security data conversationally, directly inside the RunReveal console. It executes complex queries, analyzes patterns, and guides you through investigations—all without your data ever leaving the platform.
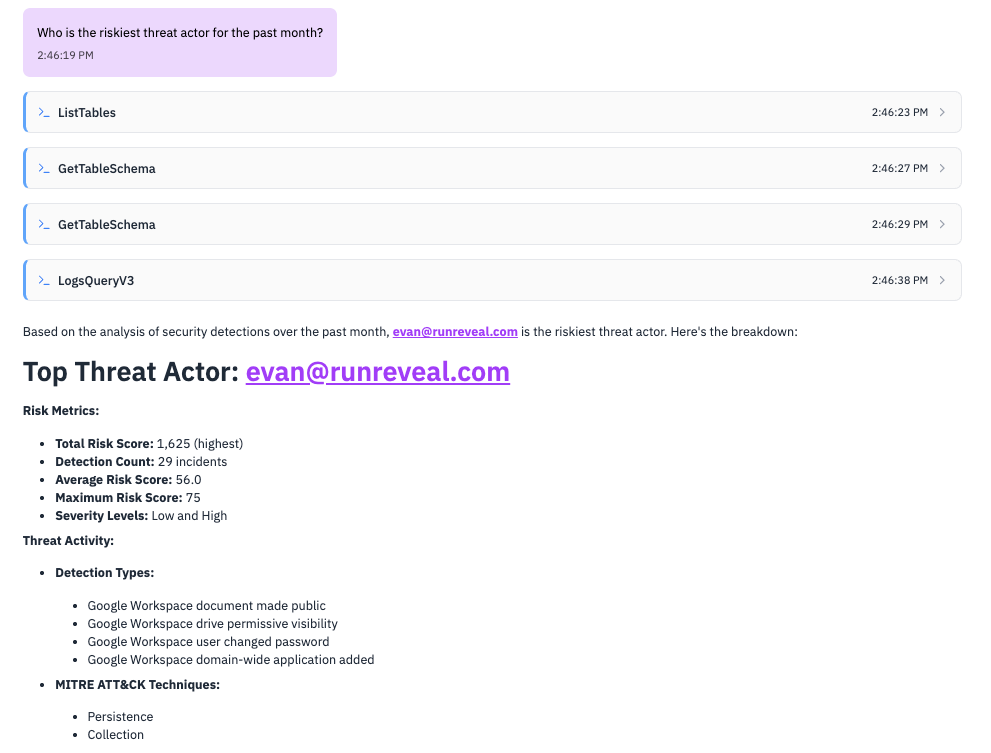
What is Native AI Chat?
Native AI Chat is fully integrated into the RunReveal UI, giving you a secure, auditable, and persistent way to investigate logs and detections using natural language. Unlike external chat clients, Native AI Chat runs entirely within your workspace, leveraging your own API keys for model access.
Why Native AI Chat?
- Direct data access: Query logs, examine table schemas, and analyze security data in real-time using the same APIs that you already use.
- Transparent reasoning: Every action is explained and auditable. See exactly why a query was run or a tool was used.
- Persistent context: The chat remembers your investigation history, enabling complex, multi-day investigations.
- Secure by design: Your data never leaves the RunReveal platform. All model calls are made server-side, using your own API keys.
What Can You Do with Native AI Chat?
Investigation Examples
- “Show me all failed login attempts from the last 24 hours”
- “Find privilege escalation events in the past week”
- “What IP addresses had the most failed authentication attempts?”
Detection Analysis
- “List all detection rules for brute force attacks”
- “Show me which detections fired most frequently this week”
- “What detection rules do we have for privilege escalation?”
Data Exploration
- “What tables contain network traffic data?”
- “Show me the schema for the authentication logs”
- “Find all unique user agents in web traffic logs”
Common Use Cases
Incident Response
“I need to investigate a suspicious login from IP 192.168.1.100” → Agent analyzes login patterns, cross-references with threat intel, suggests next steps
Security Monitoring
“Show me our top security events this week” → Agent queries multiple log sources, creates summary with actionable insights
Data Analysis
“Analyze authentication events from the past 30 days by geographic location, show me login attempts by country and city” → Agent reviews existing data, identifies trends, provides insights
Supported Model Providers
Native AI Chat supports multiple LLM providers. You can use your own API keys for:
Each model runs securely and never leaves the RunReveal platform.
The chat agent is currently written with the assumption that only a single provider will be configured at a time. Please clear out keys other than the model you intend to use.
Setup Guide: Native AI Chat
Prerequisites
- A RunReveal account with admin or API access
- API key(s) for your preferred LLM provider(s): Anthropic (Claude), OpenAI (ChatGPT), or Google AI (Gemini)
- Access to your RunReveal workspace settings
Step 1: Open AI Model Providers Settings
- In the RunReveal UI, go to Workspace Settings → AI Model Providers
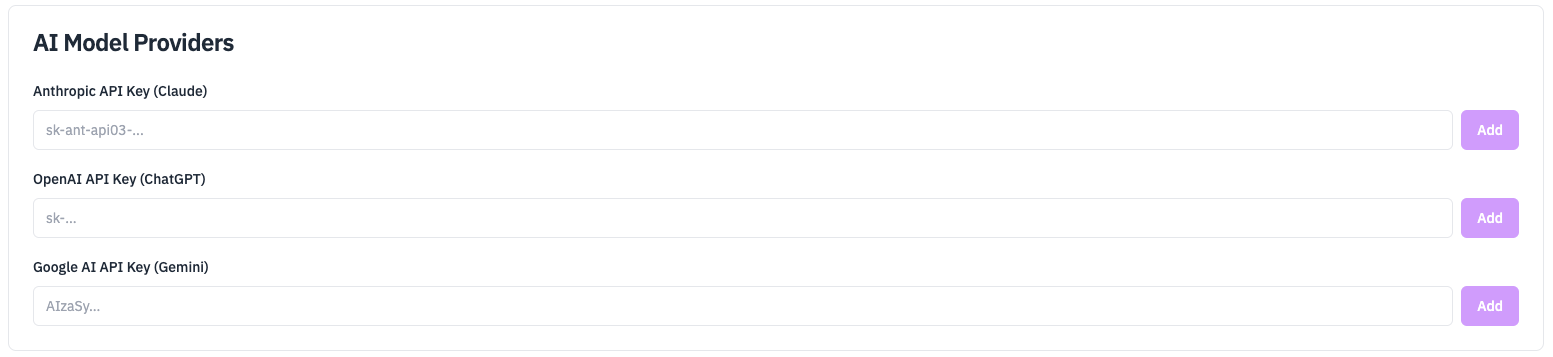
Step 2: Add Your LLM API Key
- Choose your provider (Anthropic, OpenAI, or Google AI)
- Paste your API key into the appropriate field
- Click Add
Step 3: Test API Key
- Click test button for configured LLM (if available) to validate
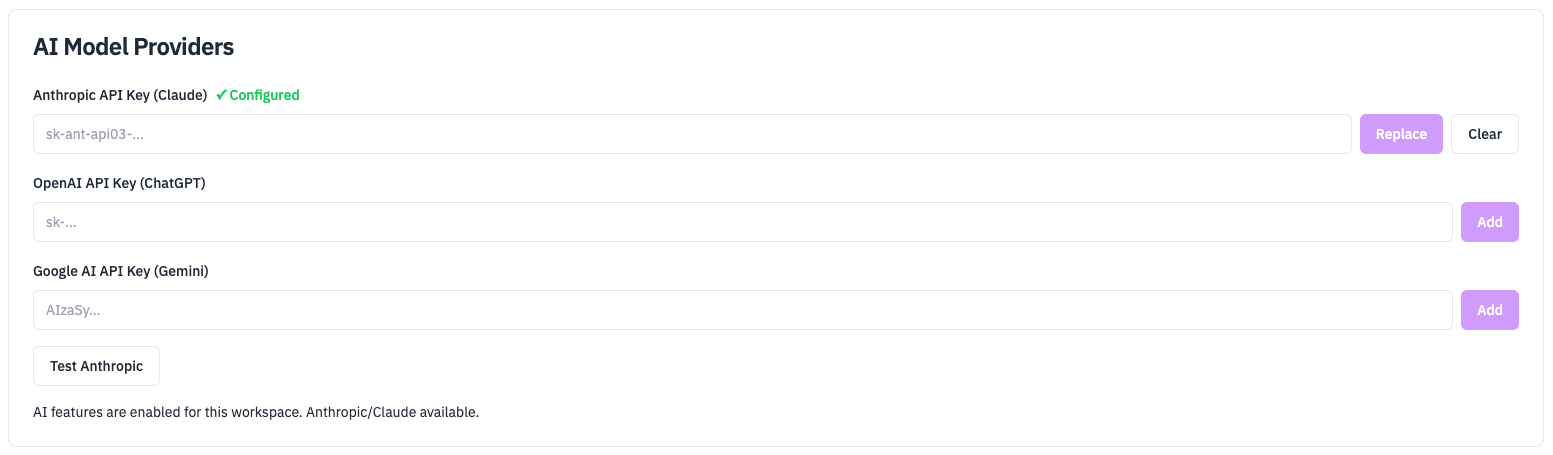
Step 4: Start Chatting
- Open the Chat tab in the UI to start chatting with prompts like “Show me failed logins from today”
Usage
Once set up, you can ask:
- “Show me all failed login attempts from the last 24 hours”
- “What detection rules do we have for privilege escalation?”
- “Create a new detection for suspicious file downloads”
- “What tables contain network traffic data?”
Native AI Chat responding to investigation prompt:
How the agent reorients after a failed query:
How It Works: The Investigation Process
Native AI Chat uses a structured approach to investigations:
Example: “Investigate failed logins from suspicious IPs”
- Observe: “Let me check your authentication logs and IP reputation data”
- Orient: “I found 50 failed logins from 3 high-risk IPs in the last hour”
- Decide: “I should cross-reference these with your user directory and check for successful logins”
- Act: Queries user tables, generates timeline, suggests blocking actions
Getting the Most from Native AI Chat
Effective Prompts
- Be specific about timeframes: “last 24 hours” vs “recently”
- Include context: “high-priority alerts” vs “all alerts”
- Ask follow-up questions: “What caused this spike in DNS queries?”
Investigation Tips
- Start broad, then narrow down: “Show me authentication events” → “Focus on failed logins”
- Ask for explanations: “Why did this detection fire?”
- Request recommendations: “What should I investigate next?”