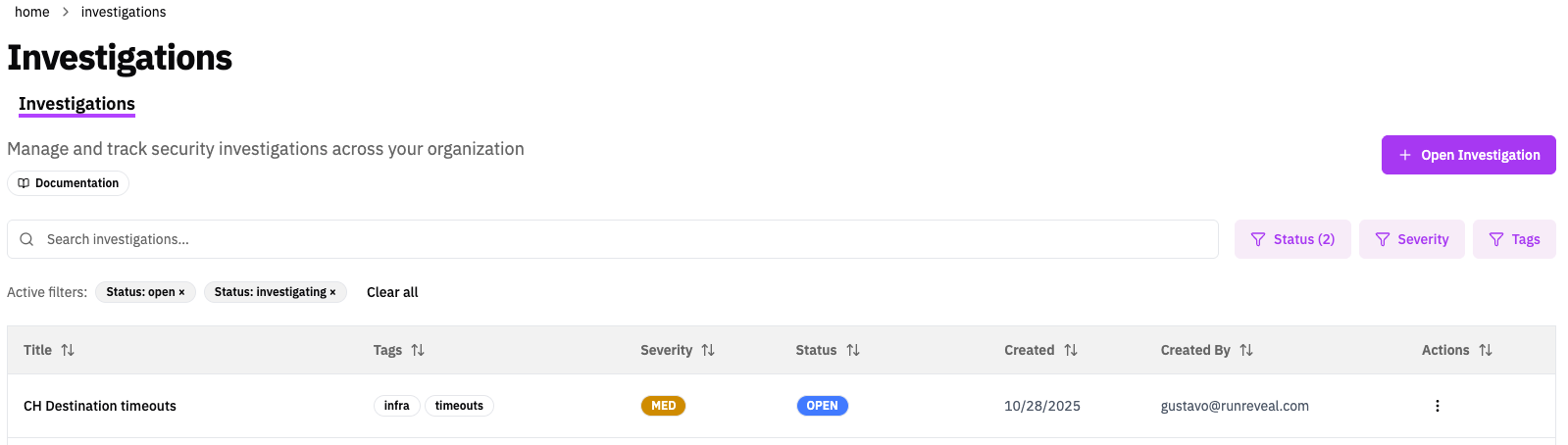
Investigations
Investigations provide a centralized workspace for tracking security incidents within RunReveal. Each investigation collects related artifacts—queries, alerts, chat conversations, and notes—into a single timeline, enabling teams to collaborate on complex incidents and maintain a comprehensive audit trail.
Check out our blog: For a deeper look at how investigations fit into incident response and automated triage—including walkthroughs and real-world workflows—see our post Introducing RunReveal’s Autonomous Security Operations Agent.
Why Investigations?
- Centralized evidence: Link queries, alerts, AI chat sessions, and notes to a single investigation timeline
- Audit trail: Every status change and artifact addition is automatically tracked with timestamps and user attribution
- Collaborative workflow: Share investigation links with team members; everyone sees the same context
- Persistent context: Investigations persist across sessions, enabling multi-day incident response
What Can You Do with Investigations?
- Track incidents from initial alert through resolution
- Document root cause analysis with timestamped notes
- Link related detections and queries for evidence preservation
Common Use Cases
Setup Guide
Navigate to Investigations
Go to Investigations in the sidebar and click Open Investigation.
Configure Investigation Details
Provide the following:
- Title: Descriptive name (required, 1-100 characters)
- Description: Context for what you’re investigating
- Severity:
low,medium,high, orcritical - Status:
open(default),investigating, orclosed - Tags: Custom labels for categorization and filtering
Start Investigating
Click Create Investigation. An initial status artifact is automatically added to the timeline. Begin adding artifacts as you work through the incident.
Investigation Properties
| Property | Values | Description |
|---|---|---|
| Status | open, agent-triage, investigating, closed | Current investigation state (agent-triage used by AI auto-triage) |
| Severity | low, medium, high, critical | Priority level for triage |
| Tags | Custom strings | Flexible labels for filtering |
| Resolution | Free text | Required when closing; documents outcome |
Artifact Types
Investigations support 10 artifact types that can be added to the timeline:
| Type | Description | How to Add |
|---|---|---|
| Note | Text comments and observations | Add Comment section on investigation page |
| Query | Links to specific queries | ”Add to Investigation” from query results |
| Query Result | Captured query results with field filtering | ”Add to Investigation” from query results |
| Alert | Security alerts related to the investigation | ”Add to Investigation” from alert detail |
| Chat | AI Chat conversations | ”Add to Investigation” from chat interface |
| Chat Message | Specific messages from chat conversations | ”Add to Investigation” from chat interface |
| Link | External URLs and resources | Links sidebar on investigation page |
| Graph | Visual graph representations | ”Add to Investigation” from graph view |
Working with Investigations
Adding Artifacts
Most RunReveal interfaces include an Add to Investigation action:
- From query results, alert details, chat sessions, or graphs, click Add to Investigation
- Select an existing investigation or create a new one
- Add an optional comment explaining relevance
- Click Add
Managing the Timeline
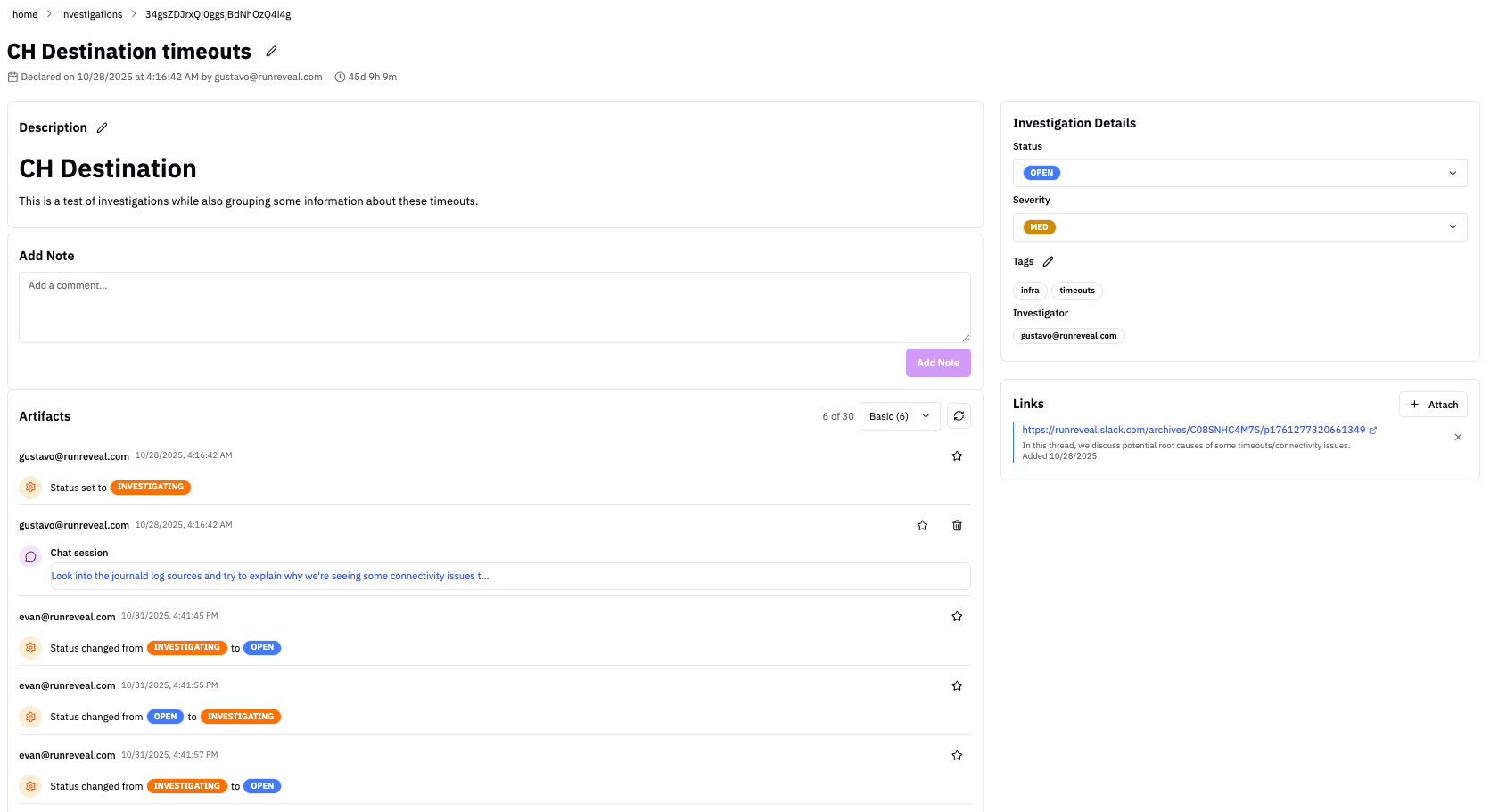
The investigation detail page provides:
- Header: Title, status, severity, duration, metadata
- Description: Editable investigation context
- Comment Section: Add notes directly to the timeline
- Artifact Timeline: Chronological view of all linked items
- Details Sidebar: Status/severity controls, tag management
- Links Sidebar: Quick links to external resources
Filtering and Starring
- Filter by type: Show only specific artifact types (alerts, queries, notes)
- Filter by starred: Surface important findings quickly
- Text search: Search across artifact comments and content
- Star artifacts: Hover over any artifact and click the star icon to highlight key findings
Closing Investigations
When changing status to closed:
- A resolution modal appears
- Enter resolution details (recommended)
- Click Close Investigation
A resolution artifact is automatically added to the timeline.
Automated Investigations
Automated investigations create and triage investigations when detection alerts fire, reducing manual work and accelerating incident response. You enable this per detection by turning on AI Triage and optionally choosing an Agent Configuration.
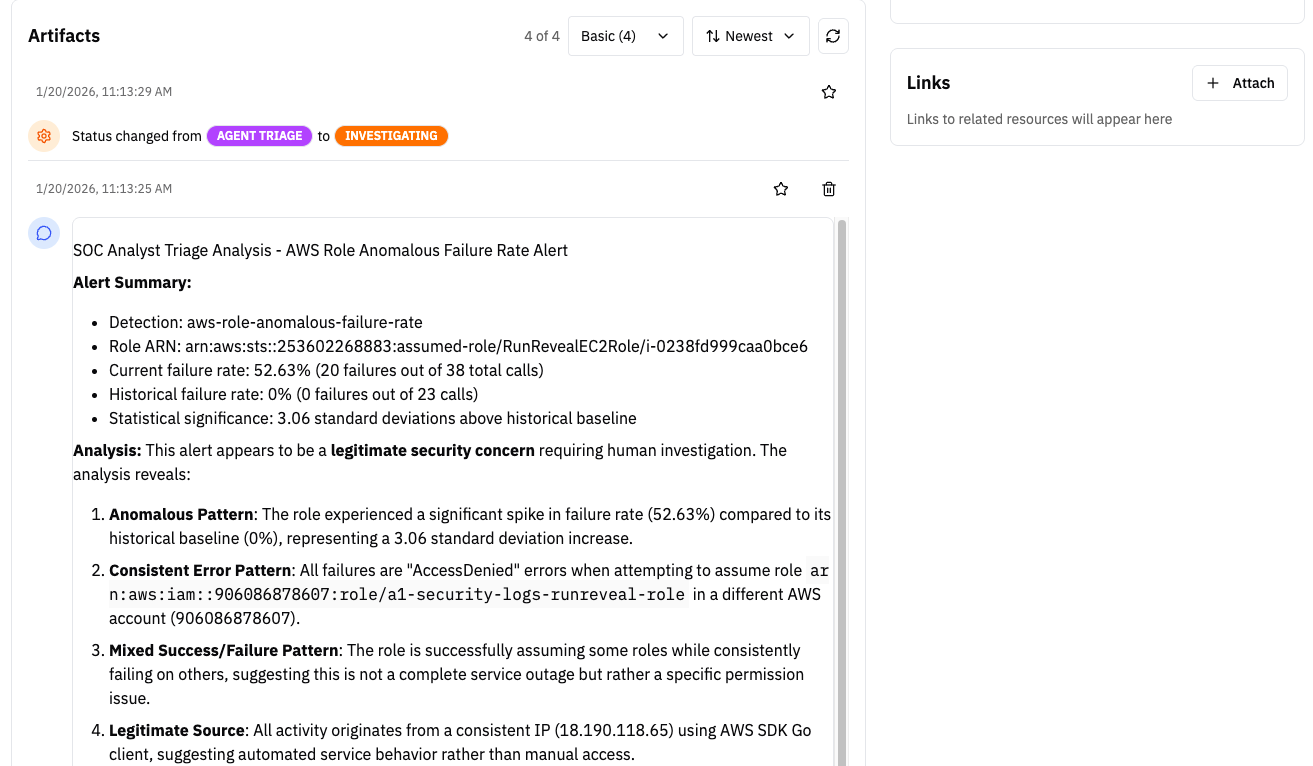
How Automated Investigations Work
When a detection alert fires and AI Triage is enabled for that detection:
-
Investigation Creation: RunReveal automatically creates a new investigation with:
- Title based on the detection name (with unique identifier)
- Alert artifact linking to the triggering alert
- Default severity (inherited from detection)
- Tags including
auto-created,alert - Status set to
open
-
AI-Powered Auto-Triage: An AI agent analyzes the alert:
- Updates status to
agent-triagewhile analyzing - Reviews the alert data and queries additional context if needed
- Adds analysis notes to the investigation timeline
- Updates severity if the initial assessment was incorrect
- Makes a decision:
- Genuine threat: Updates status to
investigatingfor human review - False positive: Automatically closes the investigation with resolution notes
- Genuine threat: Updates status to
- Updates status to

Setting Up Automated Investigations
Enable AI Triage on a Detection
- Go to Detections and open the detection you want to automate.
- Edit Detection or Edit Subscribe to open the subscription form.
- Find the AI Triage section, turn AI Triage on, and under Agent Configuration choose an agent (or leave Default Triage Agent for the built-in agent). This connects the detection to the agent channel.
- Save the detection (subscribe or update subscription).
When this detection fires an alert, RunReveal will create an investigation and run the selected agent to triage it.
Automated Investigation Flow
Scenario: A detection for “Multiple Failed Login Attempts” fires an alert.
Detection configuration:
- AI Triage: On
- Agent Configuration: Default Triage Agent (or a custom agent)
What Happens:
-
Alert fires → Detection triggers for user
[email protected]with 15 failed logins from IP203.0.113.45 -
Investigation created:
- Title: “Multiple Failed Login Attempts (a1b2c3d4)”
- Status:
open - Severity: from detection
- Tags:
auto-created,alert - Alert artifact: Links to the triggering alert
-
AI agent triages:
- Status changes to
agent-triage - Agent analyzes the alert data
- Queries additional context: e.g. “Show all login attempts for [email protected] in last 24 hours”
- Adds note: “Analysis: 15 failed attempts from IP 203.0.113.45 (previously unknown). No successful logins. Pattern suggests brute-force attack. Recommend blocking IP and reviewing account security.”
- Updates status to
investigating(requires human review)
- Status changes to
-
Analyst reviews:
- Opens investigation, sees AI analysis
- Reviews query results added by agent
- Takes action: Blocks IP, resets password
- Closes investigation with resolution: “IP blocked, password reset, account secured”
Auto-Triage Behavior: When AI Triage is enabled, the AI agent focuses only on the specific alert that triggered the investigation. It does not search for or link additional alerts, keeping the investigation scope focused.
Example: Alert Investigation Agent (create with these settings)
An agent that triages detection alerts by parsing key fields, gathering log context, enriching indicators, and producing a risk assessment with recommended actions. Use it as the AI Triage agent on detections to automate investigation creation and initial analysis.
Expand: Agent configuration to create
Use the following when creating a new agent in Agents (e.g. for Agent Configuration in a detection’s AI Triage section).
| Setting | Value |
|---|---|
| Name | Alert Investigation Agent |
| Description | An agent that triages detection alerts by parsing key fields, gathering log context, enriching indicators, and producing a risk assessment with recommended actions. Use it as the AI Triage agent on detections to automate investigation creation and initial analysis. |
| AI Prompt | 1. Triage — Parse the alert for key fields (user, IP, action, timestamp, resource). Categorize the alert type and check for known false positive patterns. 2. Gather Context — Query logs to establish baseline behavior. What’s normal for this user/system? What happened immediately before and after the alert? 3. Enrich Indicators — For any IPs, domains, or hashes, check reputation and whether they appear elsewhere in your environment. 4. Assess Risk — Weigh asset criticality, user privilege level, action severity, timing, and whether this behavior has been seen before. Use your judgment. 5. Conclude — Classify as: true positive (critical/high/medium), benign but suspicious, false positive, or insufficient data. 6. Report — Provide a brief summary, timeline of events, key evidence, and recommended actions. Use mermaid diagrams to visualize attack flows or timelines when helpful. Be direct. Lead with conclusions but don’t assume something is malicious unless it is for sure malicious. Quantify observations. If you can’t determine the answer, state exactly what additional data you need and provide next steps. If the detection / finding is bad, make recommendations for how to tune the alert. |
| Tools Needed | Add Investigation Artifact, Get Table Schema, Investigation Get, List Tables, Logs Query V3, Source List |
| Cron schedule | 0 9 * * * (9am daily, or your desired timeframe) |
| Scheduled Enabled | ON |
| Skip Permissions | ON |
Quick steps to attach to a detection (so the agent runs when the detection fires):
- Create the agent in Agents using the table above, then save.
- Go to Detections and open the detection you want to triage automatically.
- Edit Detection or Edit Subscribe to enable AI Triage for the detection and connect it to the agent channel.
- In the AI Triage section, turn AI Triage on and under Agent Configuration select Alert Investigation Agent (or the name you gave the agent).
- Save the detection (subscribe or update subscription).
When this detection fires an alert, RunReveal creates an investigation and runs the selected agent to triage it.
Type of response and artifact
The agent adds a Note artifact to the investigation timeline with a structured triage analysis. The note typically includes:
- Summary & conclusion — Classification (e.g. true positive, false positive, benign, or insufficient data) and a short narrative.
- Alert details — Detection name, severity, actor, event time, source IP, and related context.
- Baseline / context — What’s normal for the user or system and how this event compares.
- Risk assessment — Factors (actor, timing, pattern, etc.) and overall risk level.
- Recommendations — Suggested next steps and, when the alert is noisy, detection tuning ideas. The agent may include mermaid diagrams for timelines or flow.
Best Practices
Investigation Organization
- Descriptive titles: Use specific names like “2024-01-15 Brute Force from IP Range 192.168.x.x” rather than “Login Issue”
- Tag consistently: Establish team conventions for tags (e.g.,
authentication,malware,insider-threat) - Update status promptly: Move from
open→investigating→closedas work progresses - Document resolution: Always provide resolution details when closing
Artifact Management
- Add context: Include comments when adding artifacts explaining why they’re relevant
- Star key findings: Use starring to highlight critical evidence
- Link comprehensively: Add all related queries, alerts, and chats to build complete context
- Use notes for analysis: Document your reasoning and hypotheses as you investigate
Related Documentation
- Agents — Create and schedule AI agents, including for automated investigation triage
- Detections — Create detection rules that can trigger investigations
- Native AI Chat — Use AI to analyze data and add insights to investigations
- Explore Logs — Run queries and add results to investigations
- Notifications — Configure alerts that link to investigations
- Introducing RunReveal’s Autonomous Security Operations Agent (blog) — AI agent for security operations, auto-triage, and incident response